Warning: You are viewing an older version of this documentation. Most recent is here: 42.0.0
Suricata Sensors¶
This section will guide you through the possibilities and configurations scenarios for using vanilla Suricata sensors with Stamus Central Server.
Alerts Enrichment¶
If you have Suricata Sensors and would like to use alert enrichment and auto escalation in order be able to use the Hunt and STR applications, you need to do the following:
Go on
SCS->Appliances Global Settings->MaintabGo to
Suricata Sensor Alert EnrichmentSelect
Enrich and tag alerts from Suricata sensorscheckbox
NOTE Once you have selected the checkbox, you will see that there is one more option you could choose - Signature based Stamus Threat Radar.
if you select the
Enrich and tag alerts from Suricata sensorsonly, then your alerts will be enriched with specific data, such as JA3, domain, hostname breakdowns ,etc. You will be able to see this info in the Stamus Enriched Hunting application.if you select the
Signature based Stamus Threat Radaroption as well, you will also be able to use the Stamus Threat Radar application. That way specific enriched alerts will be automatically analysed and escalated by Stamus to the STR application.
Finally, you need to do an Apply changes on your SCS.
Note
In order to be able to use the Signature based Stamus Threat Radar feature, you should mandatorily add stamus.rules to the list of sources in suricata.yaml, then restart Suricata on your Custom Sensors.
Register a Suricata Sensor¶
Preparing a Suricata Sensor¶
A Suricata sensor can be any of the following major Linux distributions:
CentOS
Debian
Fedora
RedHat
SUSE
Ubuntu
that has Suricata running as a service.
On the remote (to be managed rulesets/log data) sensors you need to have the following in place:
Default Python version > 2.6 (Python 3 is not supported)
User called
amsdedicated to SCS connectionPasswordless sudo for that
amsuserThe
/home/ams/directory for that user is presentMake sure the system has
rsyncpackage installedSSH enabled
Able to start/restart/stop suricata as a service via sudo aka -
service suricata restart,service suricata start,service suricata stopSuricata config file location as follows:
/etc/suricata/suricata.yamlRule section in suricata.yaml containing only
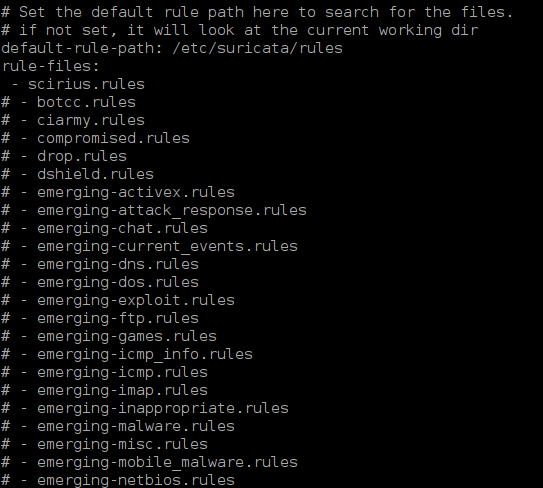
scirius.rulesfile
NOTE: Other rules need to be commented out as shown below :
NOTE: On CentOS based sensors:
The option Defaults requiretty in /etc/sudoers needs to be commented
/etc/hostname needs to be set with Stamus Central Server IP/name information for logshipping
Note
Password for ams user should be used as one time password for probe registration in the Stamus Central Server interface.
Once a Suricata sensor registration has been made the password of the ams user will be reset by SCS. After that Stamus Central Server will switch to use SSH key pair communication only.
Shipping logs from a Suricata Sensor¶
Stamus Central Server also offers the possibility to centralize logs from a remote Suriacta sensor installation. You can enable that feature at any time for a particular Suricata sensor. Please see below Step 3 (optional).
Adding a remote sensor for the first time¶
After all requirements are in place you can add the sensor to SCS as follows:
Step 1¶
In SCS - go to Appliances , on the left hand side under Appliance handling click on Add probe.
Fill in the information as on suggested/shown on the example below. Please note that you can add/chose a ruleset at a later stage if you would like:
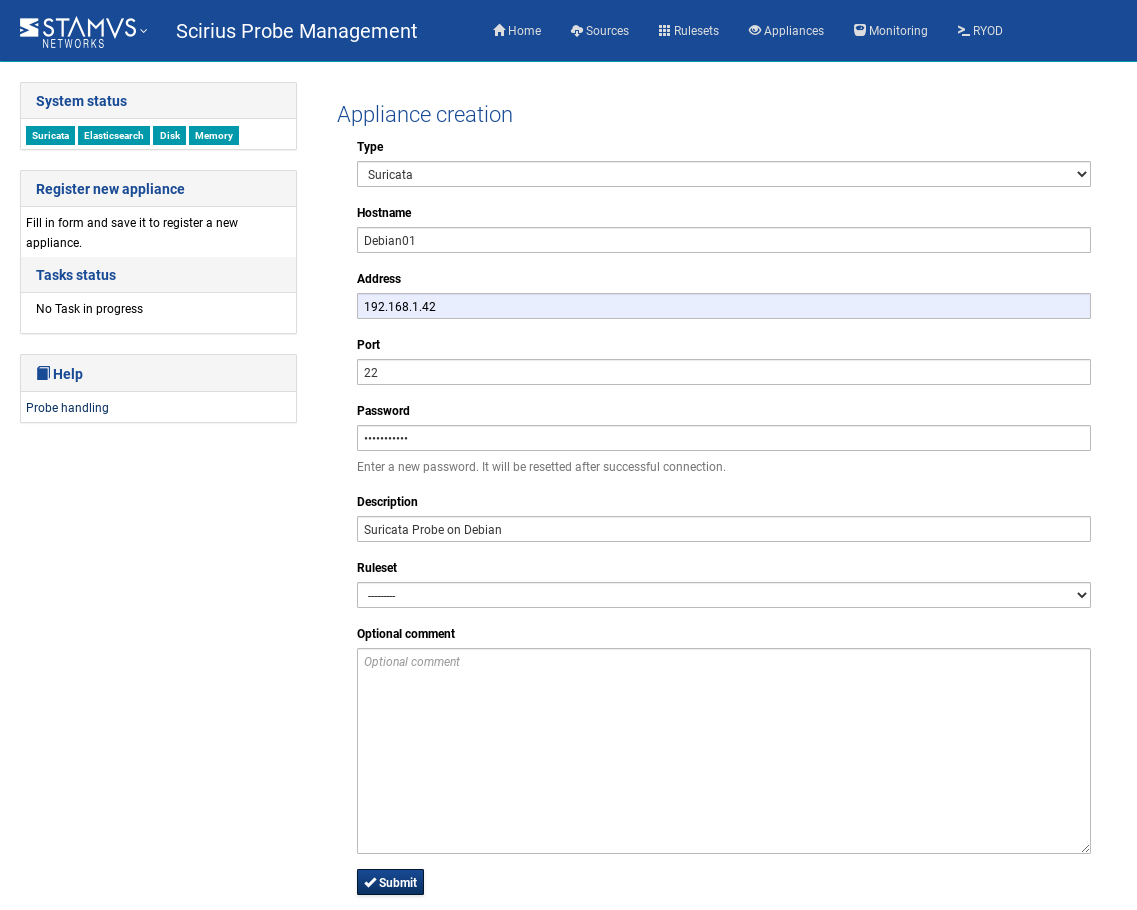
NOTE: Please make sure selected Type is Suricata for non Stamus issued appliances.
NOTE: If the remote installation has the IP address changed it will need to be reflected in these settings as well.
Step 2¶
Go to Appliances, select the newly added sensor/probe, click on Edit (under the Action tab on the left hand side),
check the information and make sure it is correct, click on Interfaces and select the sniffing interface for the probe, click Submit:
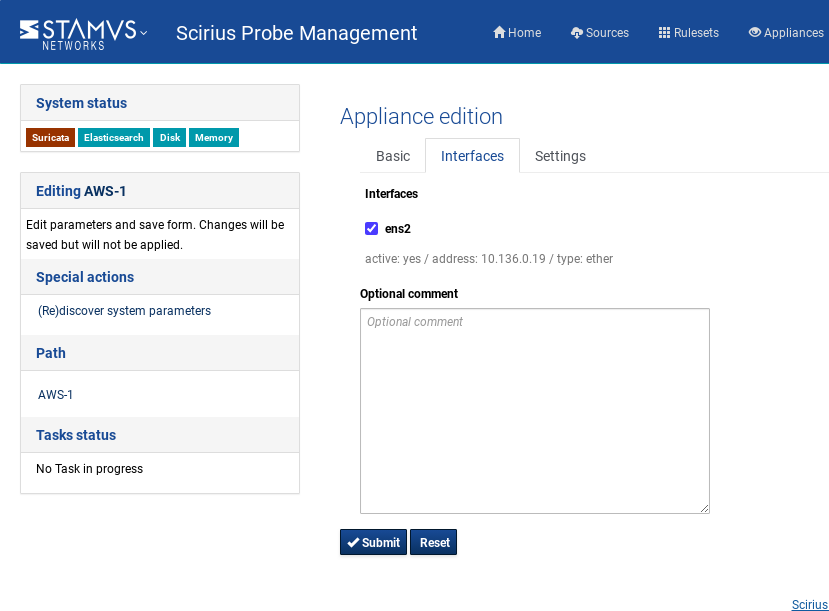
That step concludes the probe registration to the SCS for rule management.
Step 3 (optional)¶
If you would like to ship the logs from the remote Suricata sensor to Stamus Central Server go to Appliances, select the newly added sensor, click on Edit (under the Action tab on the left hand side),
check the information and make sure it is correct, click on Settings and check the box Install filebeat, click Submit. Under Pending modifications on the left hand side panel select Apply changes.
You can either schedule or apply directly.
NOTE After executing the steps above, you should do an Update/Push Ruleset in order to enable log shipping from the remote Suricata sensor to Stamus Central Server.
To do that, go to Appliances, select Update rulesets from the Action panel on the left. Then, select the relevant remote Suricata sensor from the Appliances table. Select Actions checkbox and click on the Apply button. Once the Update/Push Ruleset task is finished, logs should start coming to SCS.
