Warning: You are viewing an older version of this documentation. Most recent is here: 42.0.0
Splunk¶
Forwarding SCS logs to Splunk¶
General Procedure¶
To forward logs to Splunk, open Stamus Probe Management and go to:
Appliances
Identify the Stamus Probe you want to activate logs forwarding from
Click the
Viewbutton on the right of the screen of the selected Stamus ProbeThen, in the left-side action menu, click
Edit settingsunder theActionsectionFinally, select the
Splunktab
By default, if Splunk forwarding hasn’t been activated yet, you will only be presented one single option as illustrated by the following screenshot.
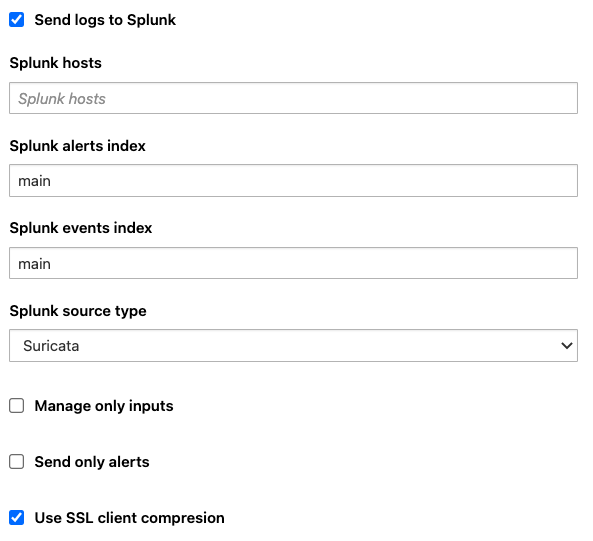
Check the box Send logs to Splunk and further options appears to configure the logs forwarding.
Note
Once the configuration fits your environment requirements, don’t forget to Apply Changes
Options¶
Option |
Purpose |
|---|---|
Splunk hosts |
Specify to which Splunk indexer the logs should be forwared to. The format is |
Splunk alerts index |
Specify in which Splunk index should the Stamus/Suricata alerts be sent to such as |
Splunk events index |
Specify in which Splunk index should the Stamus events be sent to such as |
Splunk source type |
Specifiy how to sourcetype the alerts and events sent to Splunk. If you are using the Stamus App for Splunk, make sure to adjust the sourcetype to |
Manage only inputs |
prevent SCS from overwriting the output configuration of Splunk in the output.conf file |
Send only alerts |
If enabled, only SCS alerts ( |
Use SSL client compression |
The compressed attribute only matters if you are forwarding without SSL. It determines whether Splunk will or not perform native compression on a per-data chunk (UF, LWF) or per-event (HWF) basis for outgoing data. This must be enabled on both ends for things to work. If you are forwarding with SSL, unless you explicitly set useClientSSLCompression to false, you will automatically benefit from SSL compression over the data stream. |
Verify server certificate |
If enabled, will perform a verification of both the server certificate CommonName and Alternative Name (see below) |
Server certificate CommonName |
Set the CommonName to match against the one in the certificate |
Server certificate Alternative Name |
Set the Alternative Name to match against the one in the certificate |
Client SSL key |
Upload SSL key |
Client SSL certificate |
Upload SSL certificate |
Enabling encryption with Splunk¶
To enable encryption for the Splunk connection:
Click on
Homemajor menu;Click on
Global Appliance Settings-> select tabSplunk;Enable
Connect to Splunk with SSLcheckbox;Click browse on
TLS certificate authority file of Splunk serverand upload the CA file of the Splunk server.
On Appliance edition page:
Go to
SplunktabScroll down and upload Key and Certificate files in the
Client SSL keyandClient SSL certificatefields.
When enabling SSL, do not forget to apply changes to both Stamus Central Server and Probe
Stamus App for Splunk¶
The Stamus Networks App for Splunk enables threat hunters, incident responders and other security practitioners who use Splunk to tap into the power of Stamus Central Server (SCS) or Suricata to more effectively do their job.
Stamus Networks develops advanced network threat detection and response solutions, including the Stamus Central Server and the open source SELKS.
Stamus Central Server is used by security practitioners worldwide to expose real threats to their critical assets, empower their team’s rapid response, and mitigate their organization’s risk. Its analytics engine that sits atop a unique combination of network traffic analysis (NTA), network intrusion detection (IDS) and organizational context allows users to quickly detect, investigate, and respond to threats and security policy violations.
The Stamus Networks App for Splunk allows Splunk Enterprise users to extract information and insights from both the Stamus Central Server and open source Suricata sensors. It provides dashboards and reports but also a set of commands to interact with Stamus Central Server via its REST API.
Stamus Networks App for Splunk is available on Splunkbase
Warning
The Splunk App must be deployed on the Search Head (dashboards) and Splunk Indexers (parsing)
Hint
The installation instructions, especially to integrate Splunk custom commands with SCS, are available on Stamus Networks Github.
