Declarations of Compromise®¶
Enabling or Disabling Threat Families and Specific Threats in a Ruleset¶
To enable or disable specific threat families or individual threats within a ruleset, follow these steps:
Navigate to the Rulesets Page: - Open the Management app and go to the Rulesets page.
Edit the Desired Ruleset: - Click on Edit Ruleset for the ruleset you want to modify.
Choose the Action: Under the Actions section, select one of the following options:
Enable/Disable Families: Choose this option if you want to enable or disable entire threat families.
Enable/Disable Threats: Select this option if you prefer to enable or disable specific threats within a family.
Select the Families or Threats:
Mark the relevant checkboxes for the threat families or individual threats you wish to enable or disable.
On family page, families are clickable, and show threats from this family only. This is a way to filter between all threats.
Submit Changes: - Click Submit to apply the changes to the ruleset.
These steps allow you to customize your threat detection by enabling or disabling specific threat categories or individual threats as needed.
This structure provides a clear and comprehensive guide to the Declarations of Compromise feature, covering all necessary components and interactions within the platform.
Custom DoC¶
From the Hunting interface, it is possible to create custom Declarations of Compromise (DoC) that will appear in the NDR app > Compromises > Coverage page > in the Custom Threats threat family.
Once you have created a filter that matches a specific threat in your environment, click the Policy Actions dropdown and select Create declaration events.
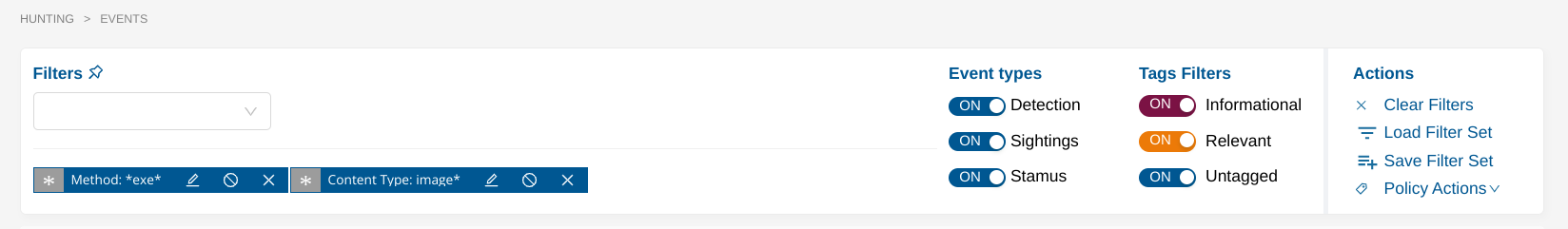
A modal will appear and let you configure the custom threat.
If the filter allows detecting an already existing threat, select that threat otherwise create a new threat by clicking on the + icon next to the Threat Name section.
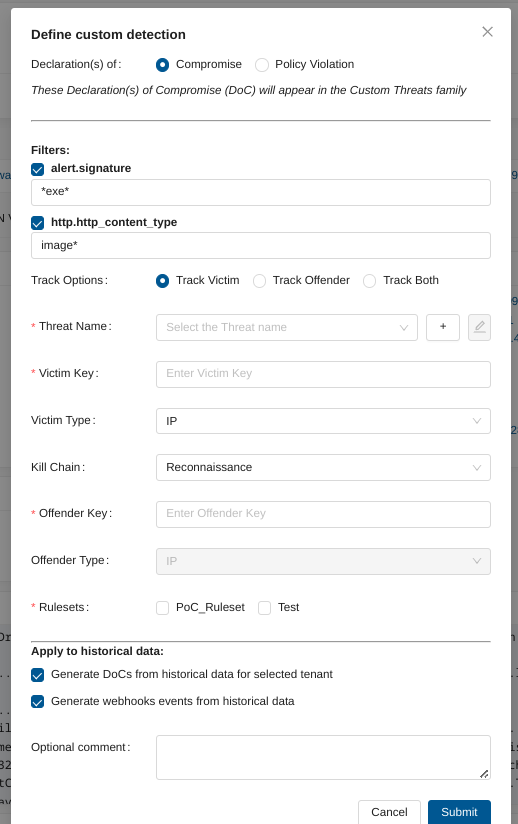
Defining Custom Detection for DoC¶
Track Options:
You have three track options:
Track Victim: Focuses on the impacted asset, with the offender type predefined as IP.
Track Offender: Focuses on the attacking entity, allowing you to select the offender type (IP, Mail, or Username).
Track Both: Tracks both the victim and offender, with flexible offender type selection (IP, Mail, or Username).
Next, you would need to fill up:
Victim Key: Set this field to the field name that represents the impacted asset, such as src_ip or dest_ip.
Victim Type: Choose the type of the impacted asset. Options include IP, Username, or Mail.
Kill Chain: Select the phase of the kill chain that this detection pertains to, such as Reconnaissance or Command & Control.
Offender Key: Specify the field name that identifies the attacking system, such as src_ip or dest_ip.
Offender Type: (Available when Track Offender or Track Both is selected) Select the offender type: IP, Mail, or Username.
Ruleset: Select one or more rulesets in which to deploy those changes.
Then, you can decide to:
Generate Declaration of Compromise from historical data
Generate workflows events from historical data
Depending on your environment, the generation of historical events may take some time. The progression can be observed under Status of tasks with a task named Stamus Events Creation (Management app > Appliances > Left Panel (Tasks) )
Important
Once a new Declaration of Compromise has been created, please update/push ruleset.
Note
Once you have created the custom DoC, you will be redirected to the Policies page, where a specific Policy action for that Declaration of Compromise will be created.
Important
Deleting the associated Policy action will automatically delete the associated custom threat.
Editing/Deleting a Custom DoC¶
From the Compromises section, go on Coverage page, then select the Custom Threats family. Click on the Threat you would like to manipulate. Once on the threat page, you will be able to edit the name, the description and additional information of that threat or delete it.
Important
Deleting the Custom Declaration of Compromise will automatically delete the associated Policy action.
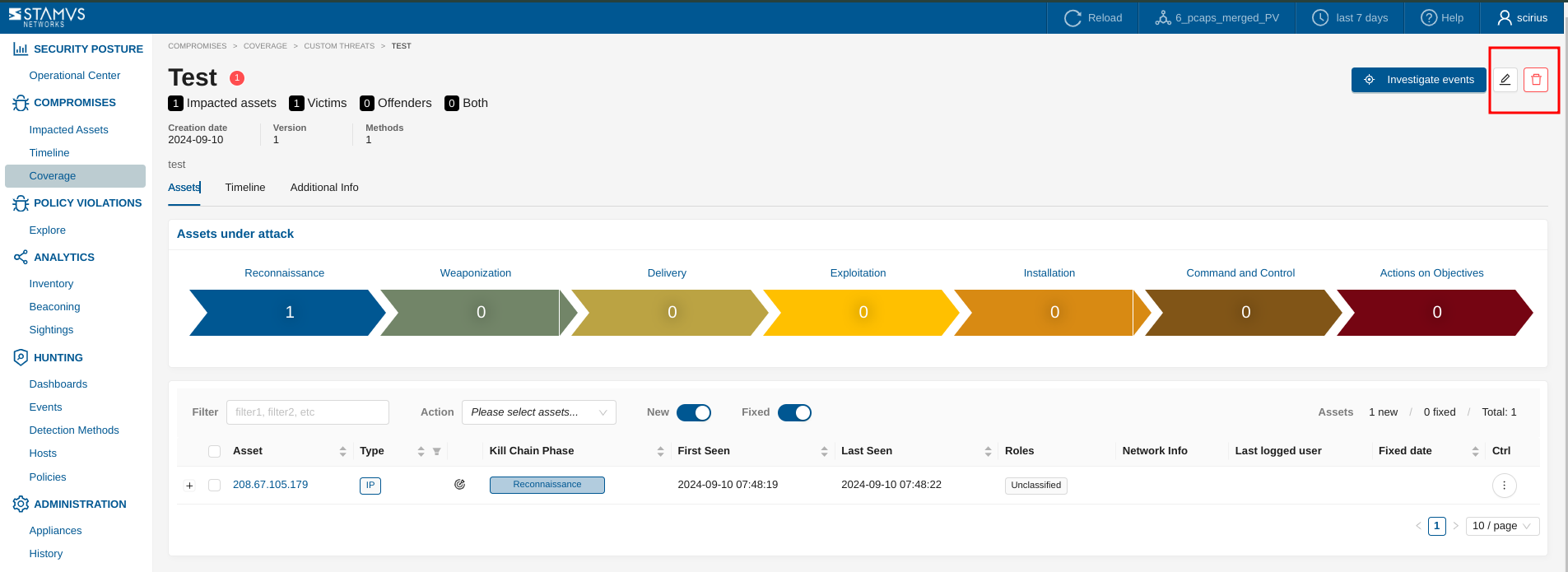
Note that the fields Description and Additional Information are Markdown compatible and images can be embedded too as in this example:
# Example
This is a serious **Threat**

DoC Suppression¶
You may decide to suppress a Declaration of Compromise from appearing. There are two approaches to creating a suppression.
Suppress By Metadata Fields Combinations in Hunting¶
To suppress specific metadata fields combinations within the Clear NDR® Central Server Platform, you can use the Hunting -> Dashboard interface. Follow the steps below to apply suppression policies based on your desired filters:
Navigate to the Hunting -> Dashboard Interface
Apply Filters of interest
Use the available filters in the Dashboard to select the metadata fields and values that you want to suppress. This can be any combination of fields relevant to your needs.
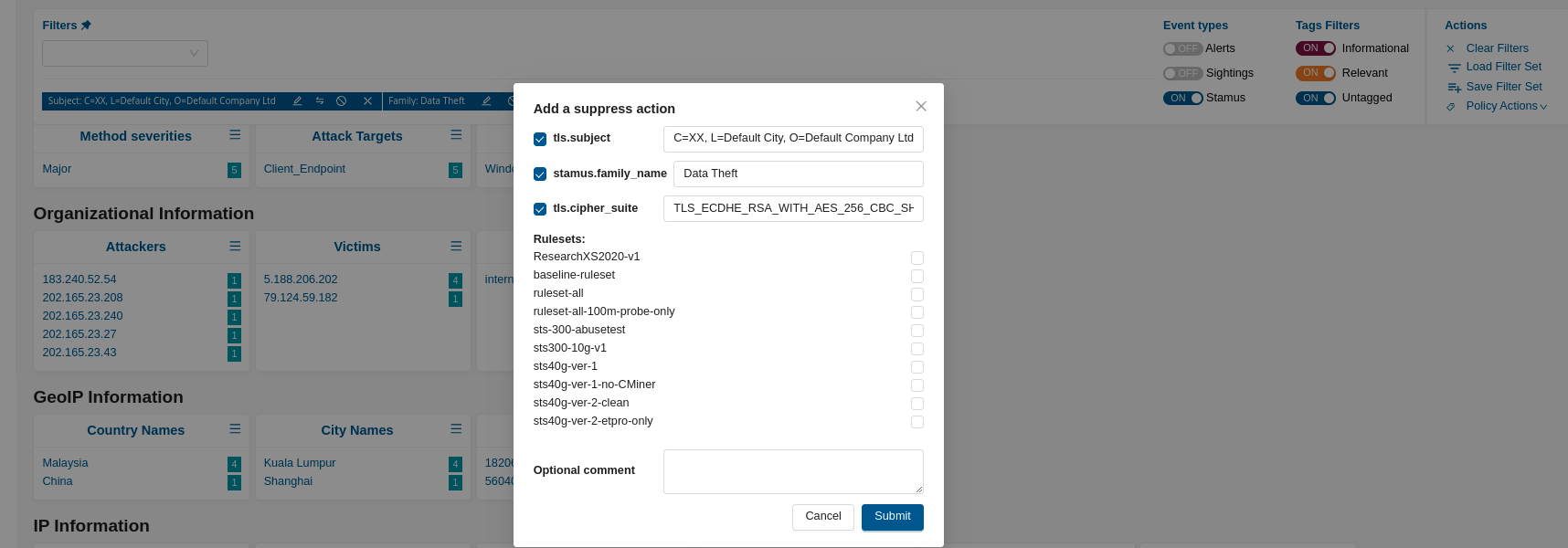
Add a Suppress Action:
Once you have applied the desired filters, open the Policy Actions menu.
Select Add a suppress Action from the dropdown.
Submit the Suppress Policy Action:
Review your suppression settings and click Submit.
Upon submission, you will be automatically redirected to the Policies page where your new suppression policy is listed.
Important
Don’t forget to update/push the ruleset to ensure that the suppression policy action is propagated throughout the system. This step is essential for your changes to take effect and be enforced during threat detection and response.
By following these steps, you can effectively suppress specific metadata fields combinations, improving the accuracy and relevance of your threat detection in Clear NDR®.
Suppress By Method ID and IP address¶
With this approach, the suppression will be performed by combining a Method ID and an IP address, or subnet, of an Offender.
To do so:
Go to Management app
Go to the Rulesets page
Click on Edit ruleset (ruleset where the DoC is deployed)
Under Expert mode, configure event suppression under Suppress events
Update/push ruleset in order to apply the suppression
suppress gen_id 2, sig_id 1002025885, track by_src, ip 107.182.230.25/8
The tracking can be either by_src, by_dst or by_either.
Note
gen_id corresponds to the gid of the signature, which is always 2 for Declarations of Compromise
Note
Variables can be used for the ip as well but make sure that this variable is defined on the probe settings
suppress gen_id 2, sig_id 1002025885, track by_either, ip $SCANNERS
Finding the Method ID¶
To find the sig_id required for the event suppression, go under Compromises and:
Go to Impacted Assets page
Choose an asset of interest from the Assets Table
Select a Threat Family and click on it
Once on the Threat page - use the Investigate events button to apply a filter on that threat
Under Hunting - go to Detection Methods page.
The filtered results will help you identify the sig_id of the appropriate signature(s) as illustrated in the following screenshot
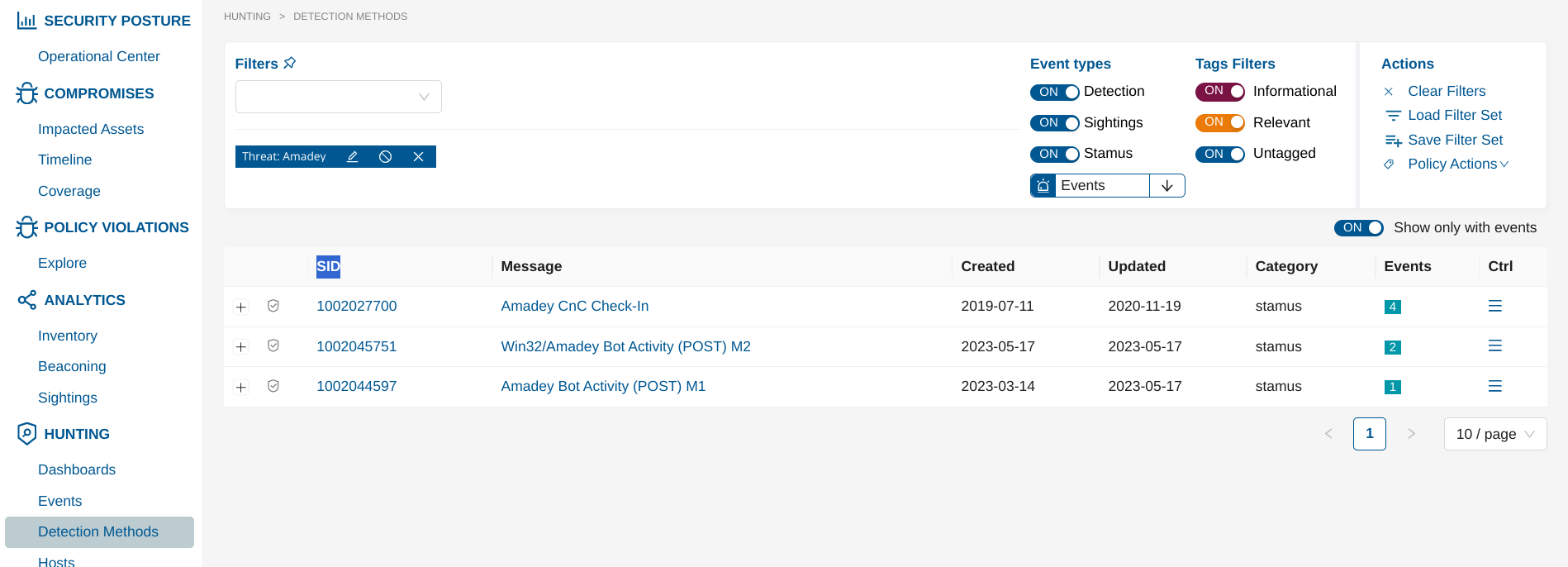
Find the Offender IP¶
To find the Offender IP required for the event suppression, go under Compromises and:
Go to Impacted Assets page
Select an asset of interest and expand it
Go to the Evidence tab
Check Attacker IPs from the table
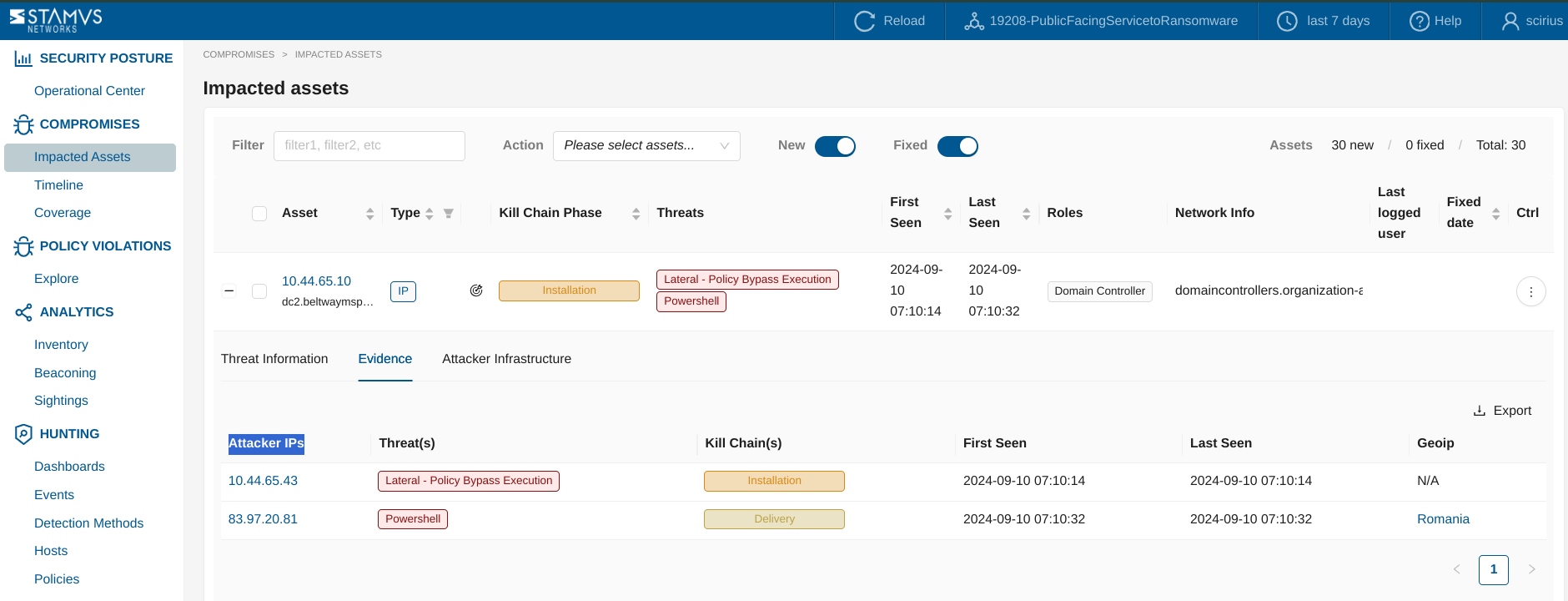
Email Notifications for DoC Events¶
The Clear NDR® Central Server (CNCS) supports sending email notifications when a Declaration of Compromise (DoC) is generated in Scirius. This feature functions similarly to webhooks, providing automated alerts to designated recipients, enabling timely response and integration into existing workflows.
To use the automated email alerts for DoC detection, you need to enable the SMTP server by going to the Management app, navigating to Global Appliance Settings, and selecting the SMTP tab to configure and enable your SMTP server settings. Once configured, email notifications for DoC events will be activated.
Example:
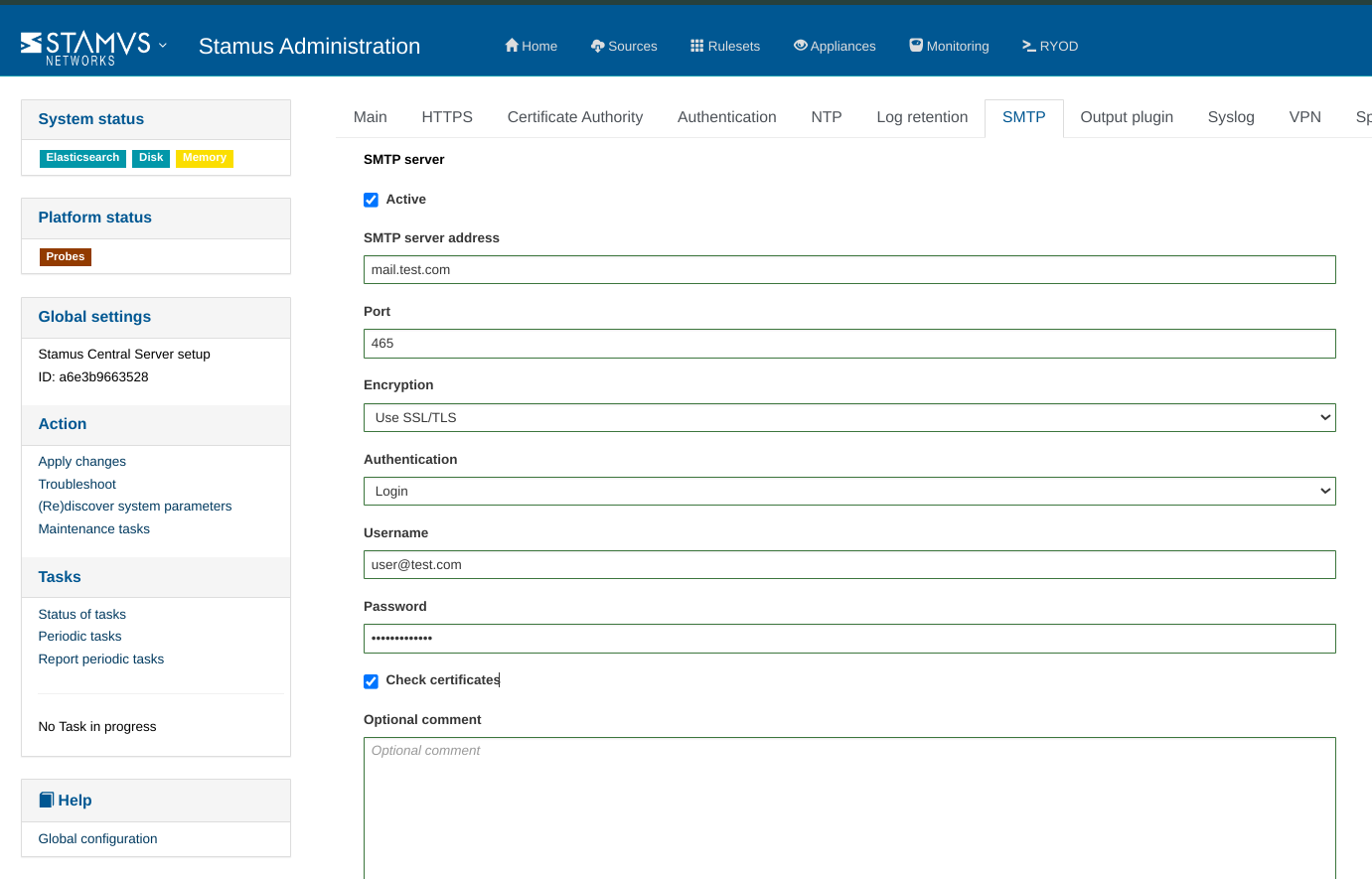
Note
Do not forget to Apply changes in order to propagate the SMTP configuration to the system.
To set up email notifications for DoC detection, from the Management app, navigate to the Integrations menu, and select the Emails tab. Then, click the Add Item button to configure the email alert settings for DoC events.
Example:
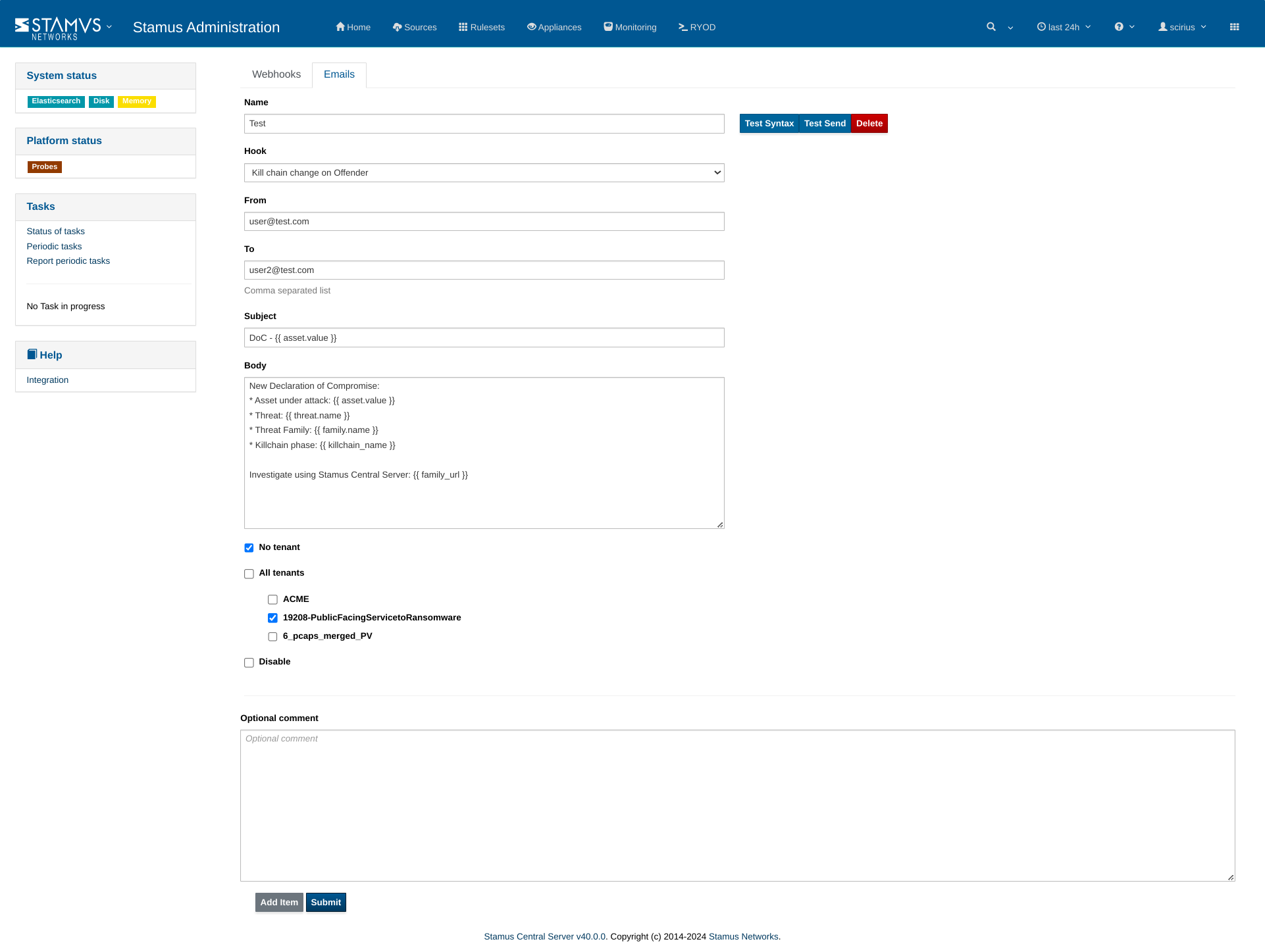
Additionally, you can configure tenant settings by selecting No tenant, All tenants, and/or specifying particular tenants as needed.
Once all information is completed, click Submit to save your configuration.
Note
An Apply changes is not needed on this step.
