Outlier Alerts¶
Introduction¶
The IDS approach is interesting and should not be disregarded but in a lot of cases, repetitive alerts that trigger at regular intervals are hiding the critical information.
Outlier alerts is a response to that issue. For every IP address and for every 8 hours time chunk of the day, Clear NDR® collects what it observes. After a few hours, the recurring behaviors of IP address will be known and after a week most user activity will be known for each IP address.
Clear NDR® tags events with each new behaviors it observes (signature for an IP on a time chunk) so it can identify new behavior associated with each assets. This will typically escalate events that will be meaningless without the characteristic of having never been seen on the host (during the associated hours of the day).
Implementation¶
The Alert Outliers algorithm is implemented in the Clear NDR® Probes and is based on the following tracking mechanism:
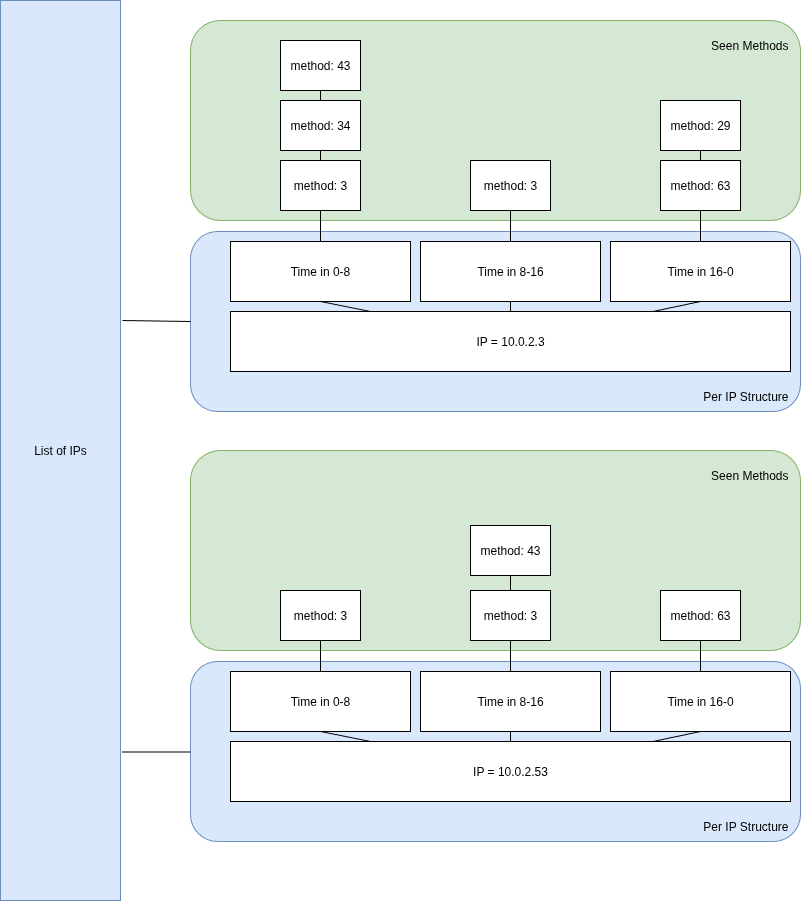
If a detection method is seen for the first time on an IP during a specific 8 hours time chunk, it is added to the structure. And the triggering event is tagged by setting
the stamus_novelty field to true.
To see only the outlier events, just activate the toggle of Outlier events in the filter bar of the Hunt part of the UI.
The stamus_novelty key is exported to the events sent outside of Clear NDR® and this allows the user to filter on these events in the SIEM or any other tools.
Clear NDR® stores the previously seen signatures using a finite element count buffer and removes the oldest events that were not seen again. This allows a natural cleaning of the behavior storage and the ability to escalate these outliers when infrequent behaviors are seen again.
