Crowdstrike¶
Host containment¶
Intro¶
This document describes using Stamus Networks’ chained webhook mechanism in order to provide integrated detection and response with CrowdStrike EDR resulting in containing (quarantining) the offending host upon Declaration of Compromise® Declaration of Compromise®.
Setup CrowdStrike authentication¶
Please generate access RestAPI keys and tokens via the official CrowdStrike site
Generated and obtain: Auth url , Client id , Client secret.
Clear NDR® Configuration¶
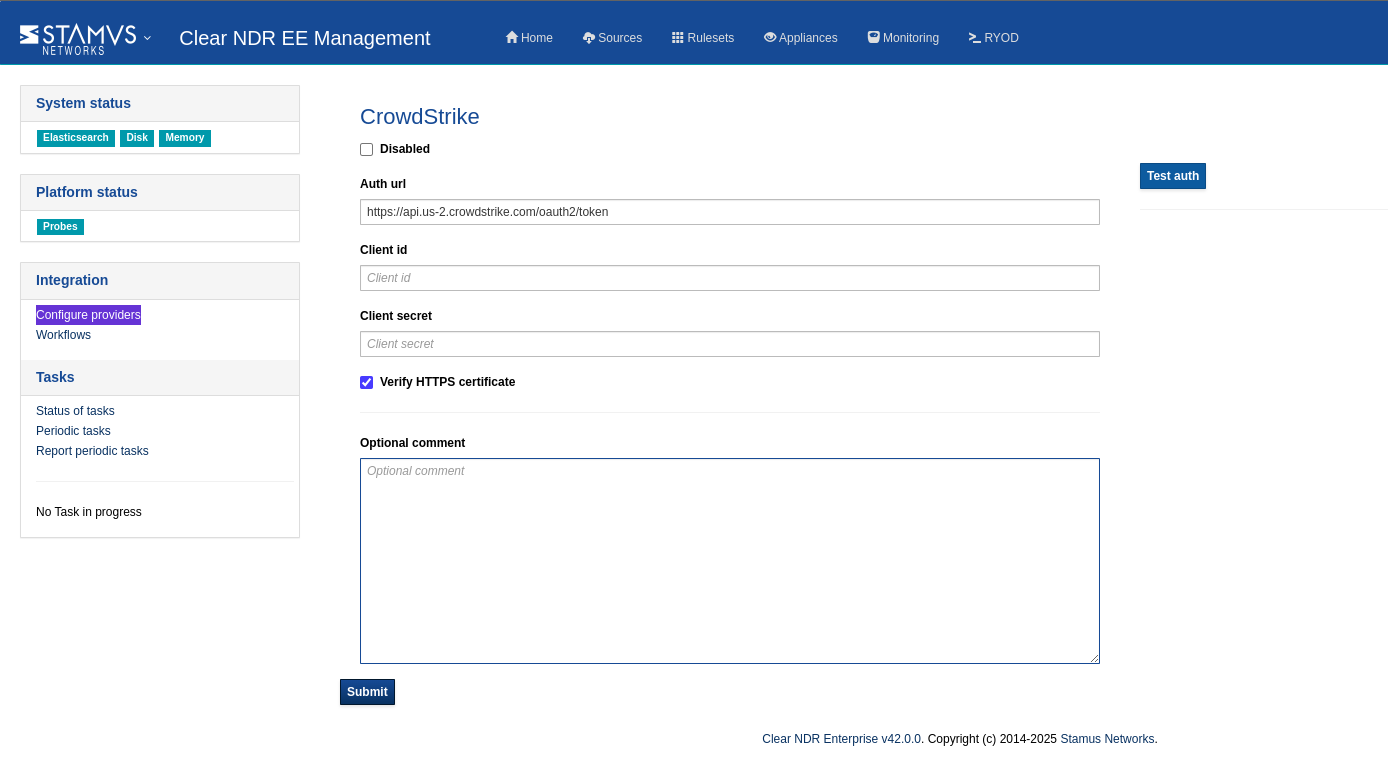
In the Administration menu , from the upper left corer drop down, select Integrations.
From the left hand side menu , select Configure providers.
Fill in the Auth url , Client id , Client secret. Click Submit.
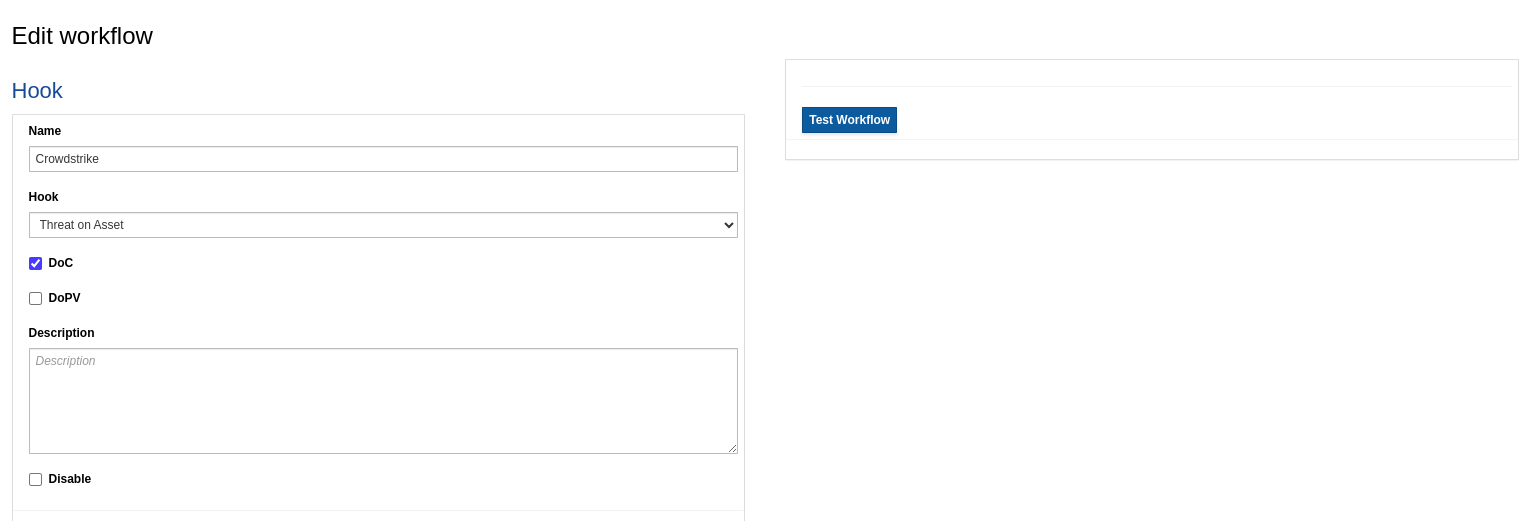
Create a workflow for the integration - In the Administration menu , from the upper left corer drop down, select Integrations.
From the left hand side menu , select Add workflow.
CrowdStrike containment needs 2 calls. The first one to get the resource id of the host. The second one to contain it - meaning a RestAPI call to block/quarantine the network on the host via the CrowdStrike falcon agent.
Select the CrowdStrike provider , select DoC type of response:
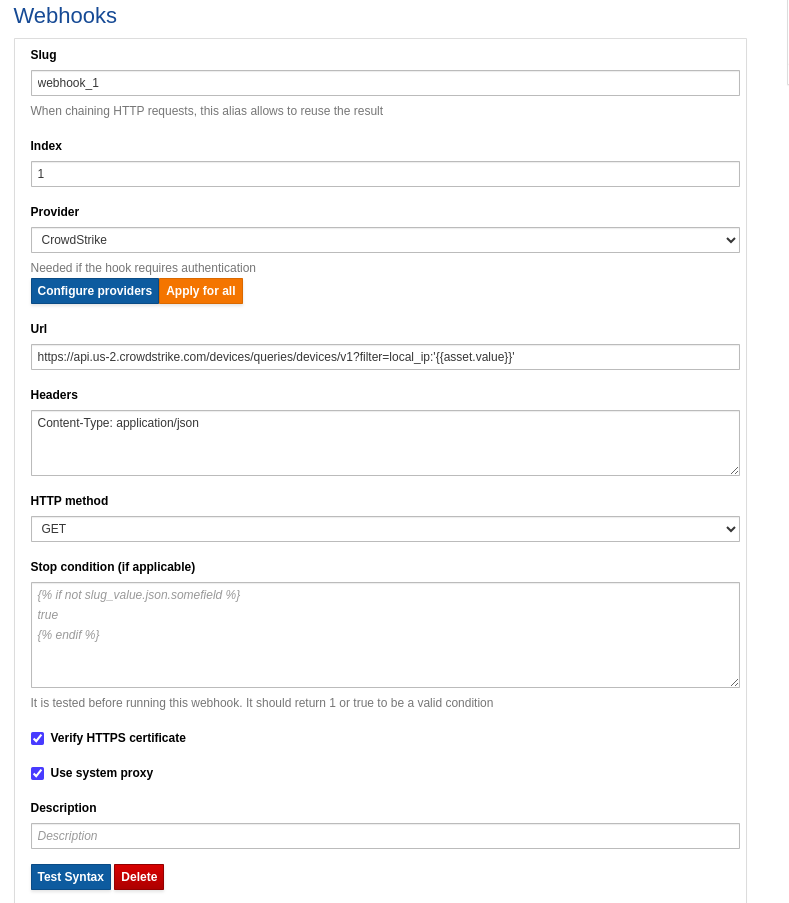
Set up one webhook to fetch the recourse id and the second one to do the action/contain.
Get the resource id¶
webhook_1: `https://api.us-2.crowdstrike.com/devices/queries/devices/v1?filter=local_ip:'{{asset.value}}'`
HTTP method: GET
Headers: Content-Type: application/json
Contain the host¶
webhook_2: https://api.us-2.crowdstrike.com/devices/entities/devices-actions/v2?action_name=contain
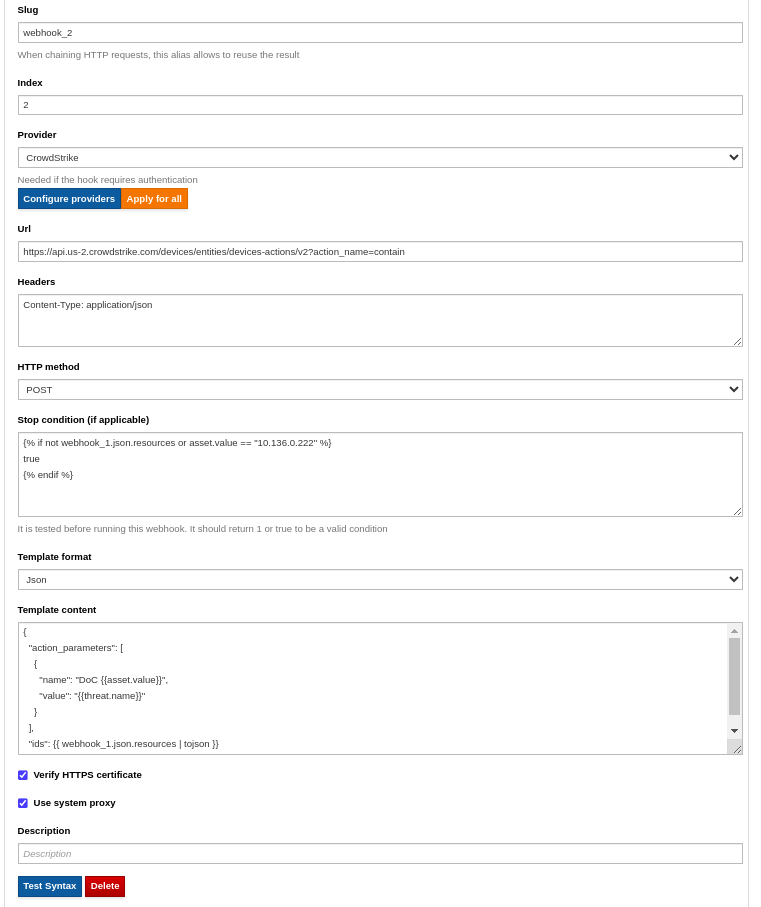
HTTP method: POST
Headers: Content-Type: application/json
Stop condition (if applicable) - meaning exclude or do not engage the response/quarantine in certain conditions.
Here multiple or conditions can be added to set exclusions, for example: or asset.value == "10.136.0.222" or asset.value == "10.136.0.223".
The first condition if not webhook_1.json.resources is set so the call is executed only if the resource id from the previous webhook_1 is available:
{% if not webhook_1.json.resources or asset.value == "10.136.0.222" %}
true
{% endif %}
Template content:
{
"action_parameters": [
{
"name": "DoC {{asset.value}}",
"value": "{{threat.name}}"
}
],
"ids": {{ webhook_1.json.resources | tojson }}
}
Verify and test¶
In this step a verification of the full sequence is triggered. In the example below the communication and process works. There is simply a stop condition that takes effect and no host is contained.
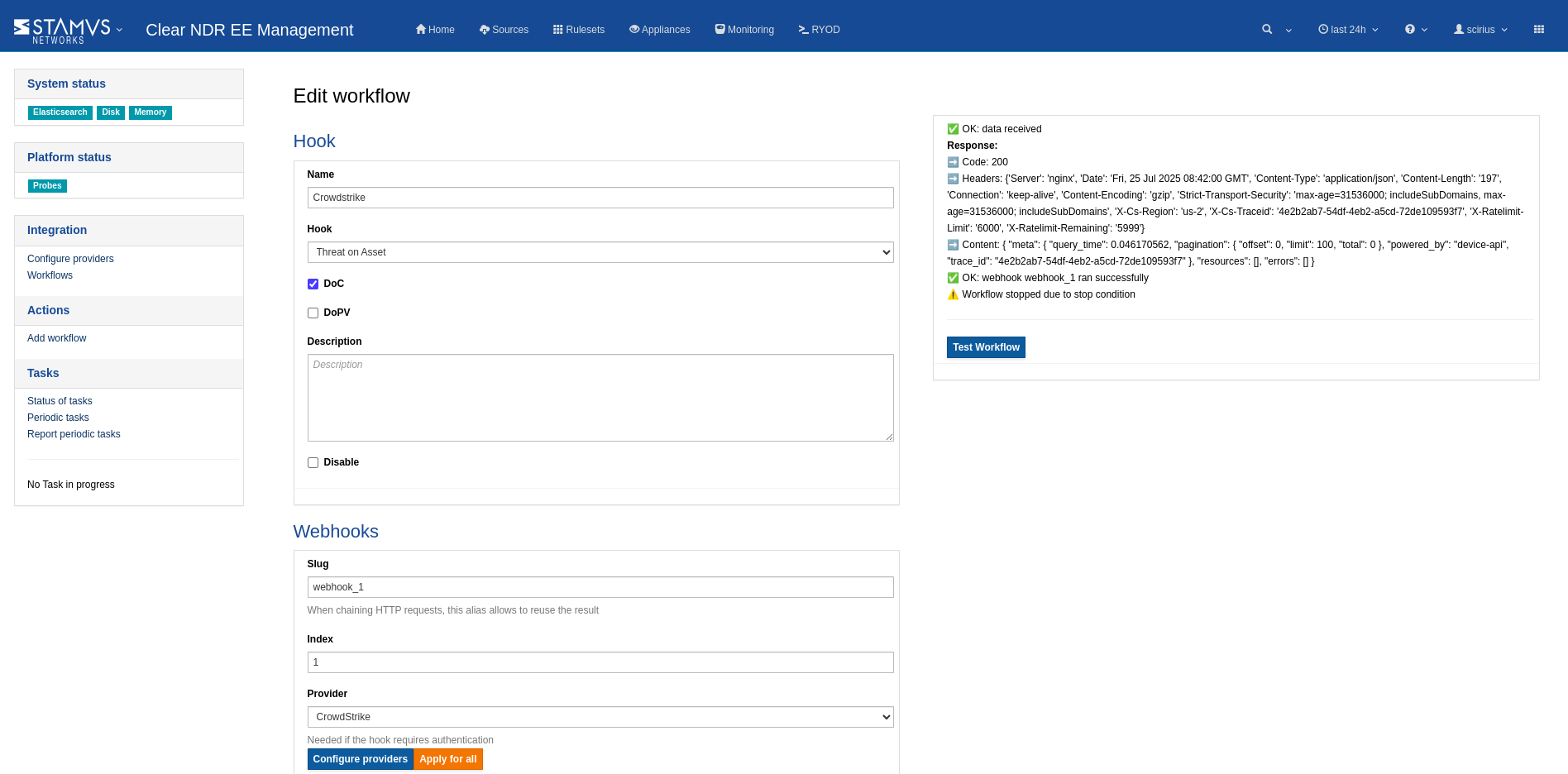
Click Submit
Additional CrowdStrike information:
Videos:
Rest API:
External Link Configuration¶
The goal of this document is to assist in configuring the Stamus Security Platform to enable the direct access to the CrowdStrike host page upon right clicking an IP.
Navigate to the external link page, by clicking External links in the
administration section on the left hand side of the hunting UI
Then click on create template:
Configure CrowdStrike IP lookup¶
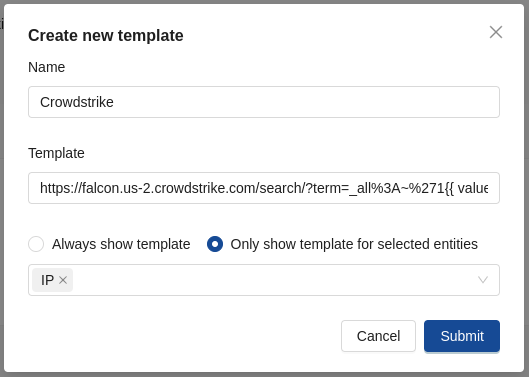
Write the following URL in the URL field:
https://falcon.us-2.CrowdStrike.com/search/?term=_all%3A~%271{{ value}}%27
The URL may change based on the location
This URL will redirect you to the host page of the selected IP in CrowdStrike Falcon.
Select Only show template for selected entities and choose IP.
Configure CrowdStrike Hostname lookup¶
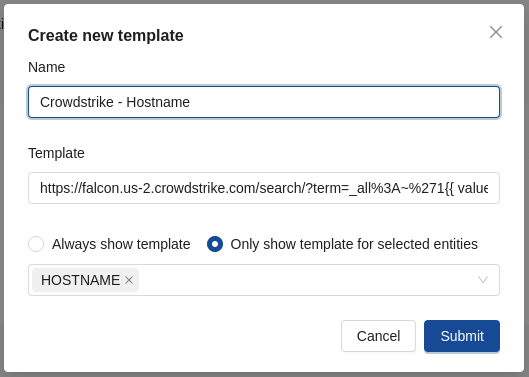
You can configure external links for hostname as well. To do so, create a new external link template.
Select a different name than those already in use
Keep the same URL as in the step before
Select
Only show template for selected entitiesand choose Hostname
The direct link to the CrowdStrike host page will be available in the following pages:
Hunting dashboard
Events
Hosts
Inventory
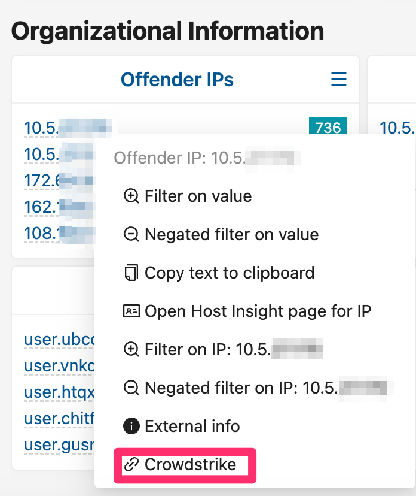
When clicking on CrowdStrike, the user will be taken to the following
page in the Falcon UI.