DoC & DoPV¶
Executive Summary¶
Clear NDR® generates two critical types of events that represent high-fidelity, asset-oriented security incidents designed to streamline threat detection and incident response: Declarations of Compromise® (DoC) and Declarations of Policy Violations® (DoPV). Both incident types share fundamental characteristics—they are asset-specific, high-confidence detections with near-zero false positives, and provide comprehensive evidence collection for effective investigation.
Declarations of Compromise(DoC) focus on security threats, detecting serious and imminent dangers such as malware, lateral movement, and advanced persistent threats (APTs). DoCs dramatically reduce alert fatigue by identifying only the most critical threats that represent true organizational compromise, transforming millions of network events into focused, actionable incidents. Each DoC maps to specific phases of the cyber security kill chain and provides complete attack timelines from initial compromise through full blast radius analysis.
Declarations of Policy Violations (DoPV) address internal compliance and security policy enforcement, identifying unauthorized activities that may not be malicious but still pose organizational risk. These include insecure protocols, outdated TLS versions, vulnerable systems, and potential data leakage scenarios. DoPVs enable continuous, real-time compliance monitoring and governance oversight.
Both event types integrate seamlessly with existing security infrastructure through SIEM integrations and automated response capabilities via webhooks. Organizations can create custom DoC and DoPV rules through an “escalation” process, extending built-in detection capabilities to address specific organizational needs. The system supports automated response workflows including incident ticket creation, endpoint isolation, IP blocking, and SOAR playbook initiation.
Overview¶
This paper describes two different types of high fidelity asset-oriented incident events generated by Clear NDR: Declarations of Compromise (DoC) and Declarations of Policy Violations (DoPV). While they share many similarities – such as those listed below, they are intended for two different primary use cases.
The common characteristics of both DoC and DoPV are:
Asset oriented - a given DoC or DoPV can only be associated with only one asset. And the complete collection of evidence and insights are associated with the asset
High confidence, high-fidelity - each of the curated threat detection methods that can initiate a DoC or DoPV incident are designed to trigger only under conditions of an active incident
Low noise - while Clear NDR® continues to record repeated detection events against a given asset, only the first one generates a DoC or DoPV and optionally initiates an automated response.
Effective with the UI or SIEM - the events sent to the SIEM contain information about the DoC/DoPV such as the status along with the first time and most recent time the threat was seen attacking the asset. Therefore, the value of DoC and DoPV can be leveraged in SIEM integrations as well as security teams who use Clear NDR® UI as their primary interface.
Built-in and/or customized - while Stamus Networks provides extensive built-in detections which are updated daily, users may create their own DoCs and DoPVs to suit the needs of their particular organizations.
The primary benefit of both DoC and DoPV is that it gives security personnel a clear starting point for what is important and worthy of investigation.
Asset-Oriented Incident Insights¶
When a DoC or DoPV event is logged, Clear NDR® collects all relevant data - including PCAPs, protocol transaction logs, flow records, and details about the threat detection logic itself – and associates it with the threat and the asset.
And the Host Insights and Timeline feature consolidates all relevant DoC and DoPV detection methods associated with an incident affecting the asset under attack. These include a complete attack timeline outlining the progression of the incident beginning with patient zero and expanding to the entire blast radius. The screenshot below illustrates the attack timeline for a DoC Incident involving multiple assets (Hosts).
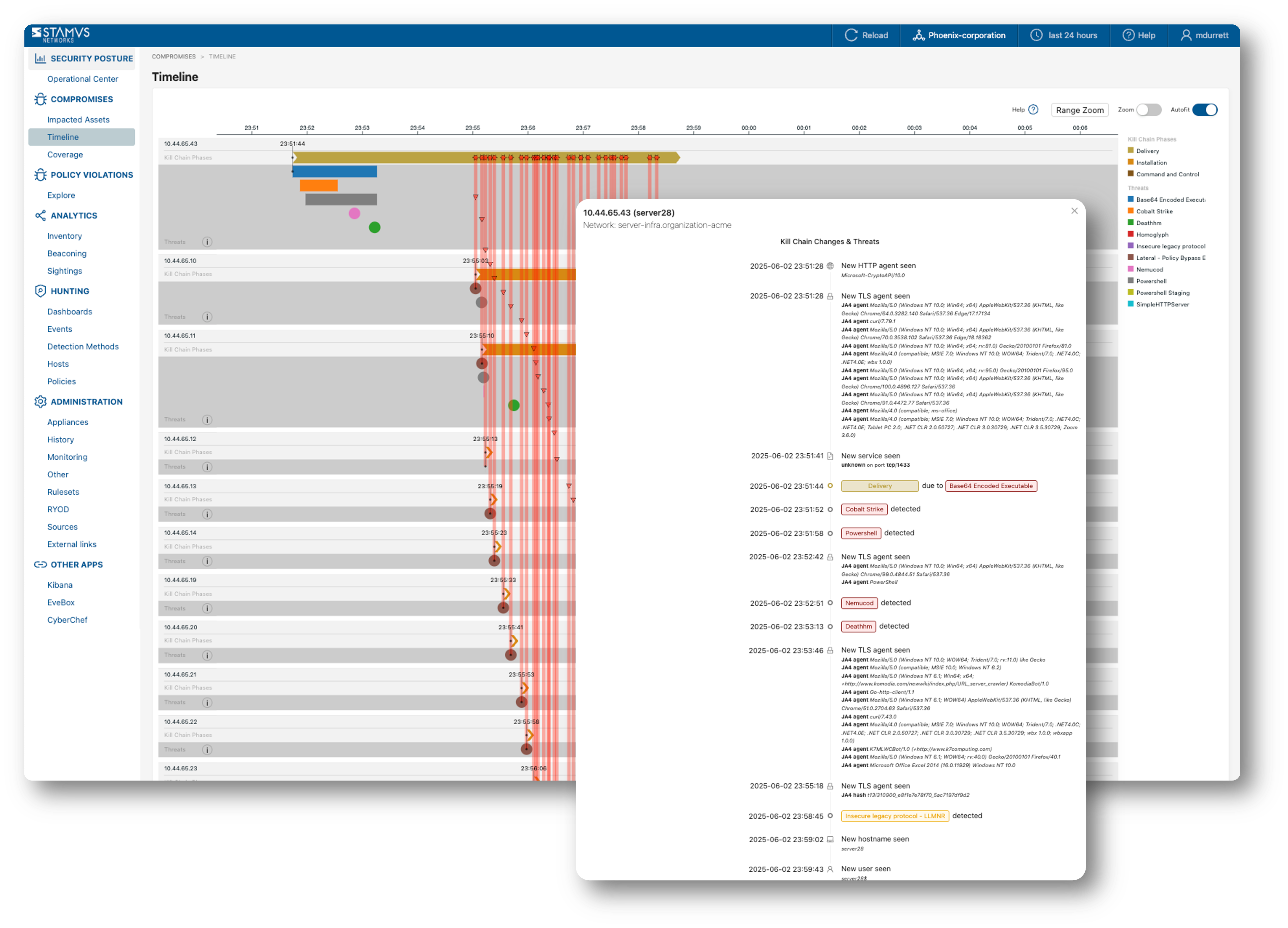
Automating Response with DoCs and DoPVs¶
DoCs and DoPVs can be used to trigger a response using an integration with an outside system such as an EDR, firewall, incident response system, or SOAR. The primary mechanism for this integration is Webhooks, a lightweight API that powers the one-way data sharing triggered by DoC and DoPV events.
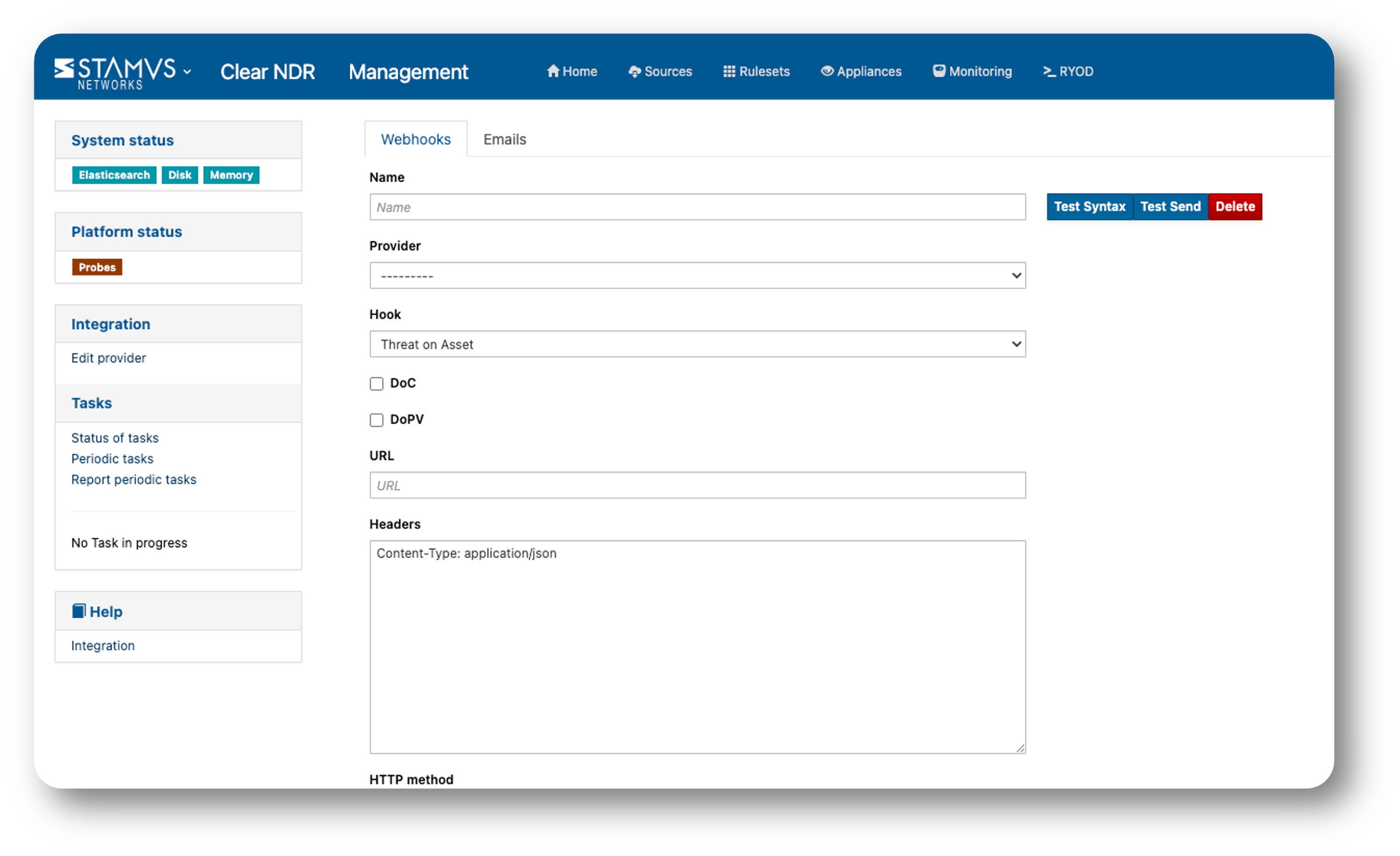
In addition to Webhooks, a DoC or DoPV can generate an email. See screenshot below.
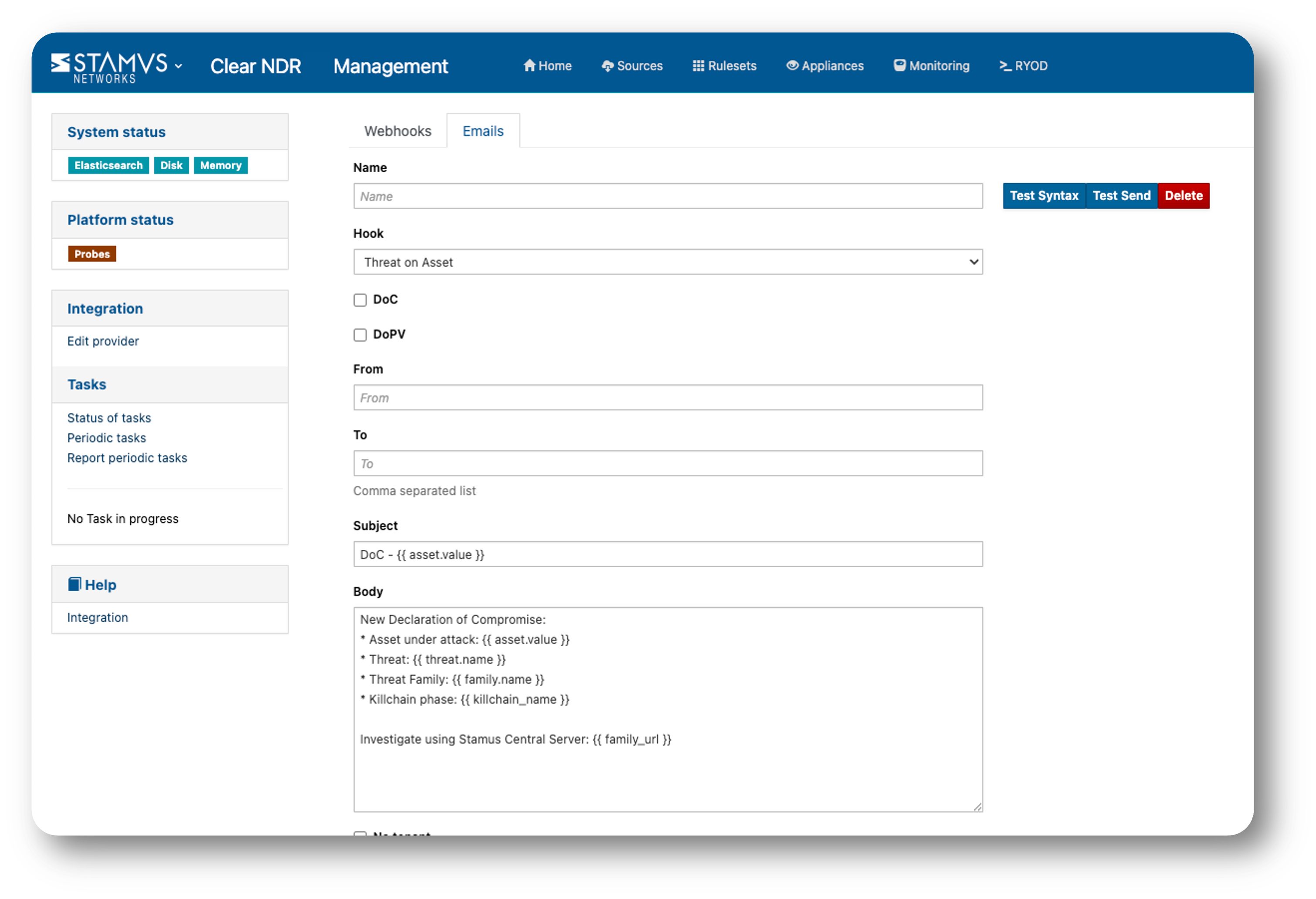
Examples of common webhook integration use cases for DoC include the following:
Open an incident response (IR) ticket ticket via an IR system
Isolate an offending endpoint via an EDR (endpoint detection and response) system
Block an offending IP Address via a firewall rule
Initiate a response playbook via a SOAR (security orchestration and response) system
Send a message to your instant messaging platform of choice (Slack, Teams, WhatsApp, Google Chat…)
Reviewing the Power of DoCs and DoPVs¶
Clear NDR’s Declarations of Compromise and Policy Violations represent a paradigm shift from traditional security monitoring approaches, providing security teams with precise, high-confidence starting points for investigation rather than overwhelming them with low-fidelity alerts. By focusing on asset-oriented incidents with comprehensive evidence collection, these detection events bridge the gap between raw network data and actionable security intelligence.
The dual approach addresses both threat detection (DoC) and policy compliance (DoPV), creating a comprehensive security posture management solution. The system’s integration capabilities—spanning SIEM platforms, automated response systems, and custom DoC and DoPV escalation creation—ensure that organizations can adapt these high-fidelity detections to their specific operational workflows and security architectures.
Ultimately, DoCs and DoPVs transform security operations from reactive alert processing to proactive incident management, enabling security personnel to focus their expertise on genuine threats and policy violations while maintaining the detailed forensic capabilities necessary for thorough investigation and response. This approach significantly enhances both the efficiency and effectiveness of modern cybersecurity operations.
