Warning: You are viewing an older version of this documentation. Most recent is here: 42.0.0
Hunting¶
Introduction¶
Hunting is an interface dedicated to Threat Hunters and Cybersecurity Analysts for Detection Methods, Events, Sightings, Host Insights, events and services visualization and tuning.
Hunting uses a drill down approach to select events. Filters on metadata contained in the alerts events can be simply added by clicking on the magnifier icons next to the field value.
Once a composite filter is defined, the user can take an action based upon it. The action will be applied to all future events matching the composite filter.
In Enterprise Edition, Stamus probes can have actions/classifications applied for custom defined filters that are based on metadata.
It is easy to create a detailed filter that actually encompasses a lot of verbose/informational events that do not need further investigation. You can then choose to create an action that will classify any such events automatically in the future. To do so, click on Actions button in the right upper corner of the Hunt page. Select Tag, select the desired ruleset(s) for inclusion, click on Submit, click on the Update threat detection button icon on the top bar, right hand-side of the page, right next to the History button. By repeating that process for other relevant events, the system would eventually heal itself by classifying all the required data.
This comes with a great benefit of being able to filter out all informational classified events just by enabling/disabling the Informational switch (upper bar of the Hunt screen). Now you can concentrate on threat hunting the rest of the events - those that have not been classified Untagged and/or those that have already been classified as Relevant.
Understanding the search¶
Basic¶
When a magnifier button is used, a full string search is done on the key and value. This search can be edited (via the pen icon) to change the content. It will remains a full
string match as long as the wildcard search option is not activated.
Wildcard search¶
In Wildcard Searches - is possible by using either the * or the ? characters to search a substring.
Wildcard search is using a word tokenizer. By consequences, spaces are not allowed in wildcard search.
If you would like to search on a more complex strings containing whitespaces, as for example: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1), your search will have to be separated into 2 different filters:
Filter on
*mozilla*, and,Filter on
*windows*
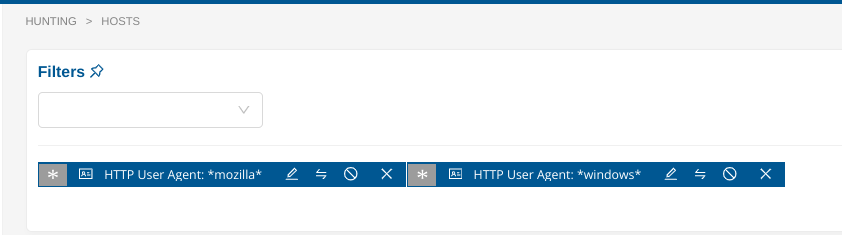
This is needed, due to some Elasticsearch specifics/restrictions. Thus, the search filter has to be matched on word boundaries.
Please also note that search filter are case insensitive.
Here is an example search on a specific type of Issuerdn for Certificates in use:
If you would like to search for all the issuerdn that contains search on *modo* would return:
issuerdncontaining:COMODOissuerdncontaining:Comodoissuerdncontaining:comodoand strings only, surrounded by spaces:
C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Extended Validation Secure Server CA
Search on *.com would return:
issuerdnending with:.com
Search on Google* would return:
issuerdnstarting with:Google
Note
You could also combine Wildcards when necessary
Search on ?oogle* would return:
issuerdnstarting with:Googleissuerdnstarting with:GOOGLEissuerdnstarting with:gOoGlEetc.
Host ID search¶
If understanding host ID search is obvious in the Host ID page as it is just a match on fields inside the host ID entries, their impact in other pages is really different. When a host ID filter is activated on a page like Alert, Hunt displays the alert events for the set of IP addresses matching the host ID filter. So for instance, if you want to see the attack on your Apache servers, just search for this HTTP server in host ID page and witch to the Events or Detection Methods page.
Convert Host ID from/to alert search¶
Some fields are available in host ID and alert events. It is thus possible to switch from a search on host ID fields to a search on alert fields.
The interface allows this by clicking on the migration icon displayed on the right part of compatible filters.
Keyboard shortcuts¶
Tag filtering¶
Here is the complete list:
A: display all events
R: display only Relevant events
I: display only Informational events
U: display only Untagged events
Hunting Examples¶
Search by name¶
It is quite easy, regardless of the number of events, to search, whether a specific threat is present. Go to the Dashboard page, choose Message from the drop down menu at the top left corner of the page, type in Emotet, hit Enter on your keyboard. This will display any alert events and their related metadata, for any Signature that has alerted and contains the word Emotet in its message.
Hunt by IP¶
To simply filter on all events from or to a specific IP, you can go to Dashboard, Detection Methods or Hosts page, choose IP from the drop down menu at the top left corner of the page, and enter/paste the IP of interest, hit Enter on your keyboard.
Host intel triaging¶
If you have an IP search filter set in the Dashboard or Detection Methods pages, you can switch (by simply clicking on it) to the Hosts page. The result will display all hosts that have alerting events from or to that specific IP. You can further choose a host and expand in details its threat intel data gathered to further improve the investigation.
Unusual useragents¶
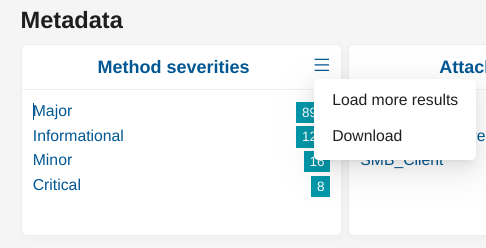
In the Dashboard page - scroll down to the HTTP Information panel, go to Useragent , click on the right upper corner of the box, click Load more results. Investigate the useragent names present. Look for suspicions/nontraditional names. To create a filter for a specific useragent - simply click on the magnifier icon, next to the field value. This will result in events and their metadata specific to that useragent. You can then go to Events page by simply clicking on it (left hand-side part of the current view). This will render all alert events relevant to that useragent.
Unusual domains¶
In the Dashboard page - scroll down to the DNS information panel, go to Name , click on the right upper corner of the box, click on Load more results. Investigate the domain names present. Look for suspicions/nontraditional/random names. To create a filter for a specific domain - simply click on the magnifier icons next to the field value. This will result in events and their metadata specific to that domain. You can then go to Events page by simply clicking on it (left hand-side part of the current view). This will render all alert events, relevant to that domain name.
Flip the search¶
In the Detection Methods page, choose Events min from the drop down menu at the top left corner of the page, type in 1, hit Enter on the keyboard. Now select Events max type in 5, hit Enter on the keyboard. This will result in displaying all detection methods that have triggered between 1 and 5 events for the specific timespan. You can further choose to order them by asc or desc order, name, message or created date. That way you could aim at investigating low noise alert events.
To create a filter for a specific detection method - simply click on the magnifier icon on the right hand-side of the displayed row. Then you can simply switch to Events page to see actual event examples or switch to Hosts page to see IP/host based threat detection profiling for that specific signature.
Find Alert events by Policy Actions¶
If you have multiple Policy Actions and want to find out which one has triggered an Alert Event, you need to do the following:
go to Events page in Hunting -> click on the Event of interest to unfold it
click on Json View tab and look for the
rule_filter_<number>:
"tag":"rule_filter_9"
use the following REST API endpoint to retrieve information on the rule filter
https://10.136.0.27/rest/rules/processing-filter/9/
Note
The above is an example link. 10.136.0.27 is the IP of SCS and 9 is the number of your rule filter.
scroll down to Filter defs form. There you will find information on:
Policy Action type (Tag, Tag and Keep, Suppress, etc.)
Options (Relevant, Informational)
Ruleset
Index - this is the index of the Policy Action
go back to Hunt -> Policy Actions tab
at the far right of the table, you will find the relevant indexes of your Policy Actions
Host ID basic search techniques¶
On Hosts page, you are able to use different search techniques to narrow down the results. It is possible among other things to search for hosts with a minimum or maximum count of services, as well as selecting hosts that run a specific version of an HTTP server. You can also simply look for hosts where a user (identified by its username) did connect.