Warning: You are viewing an older version of this documentation. Most recent is here: 42.0.0
The Most Powerful Capabilities¶
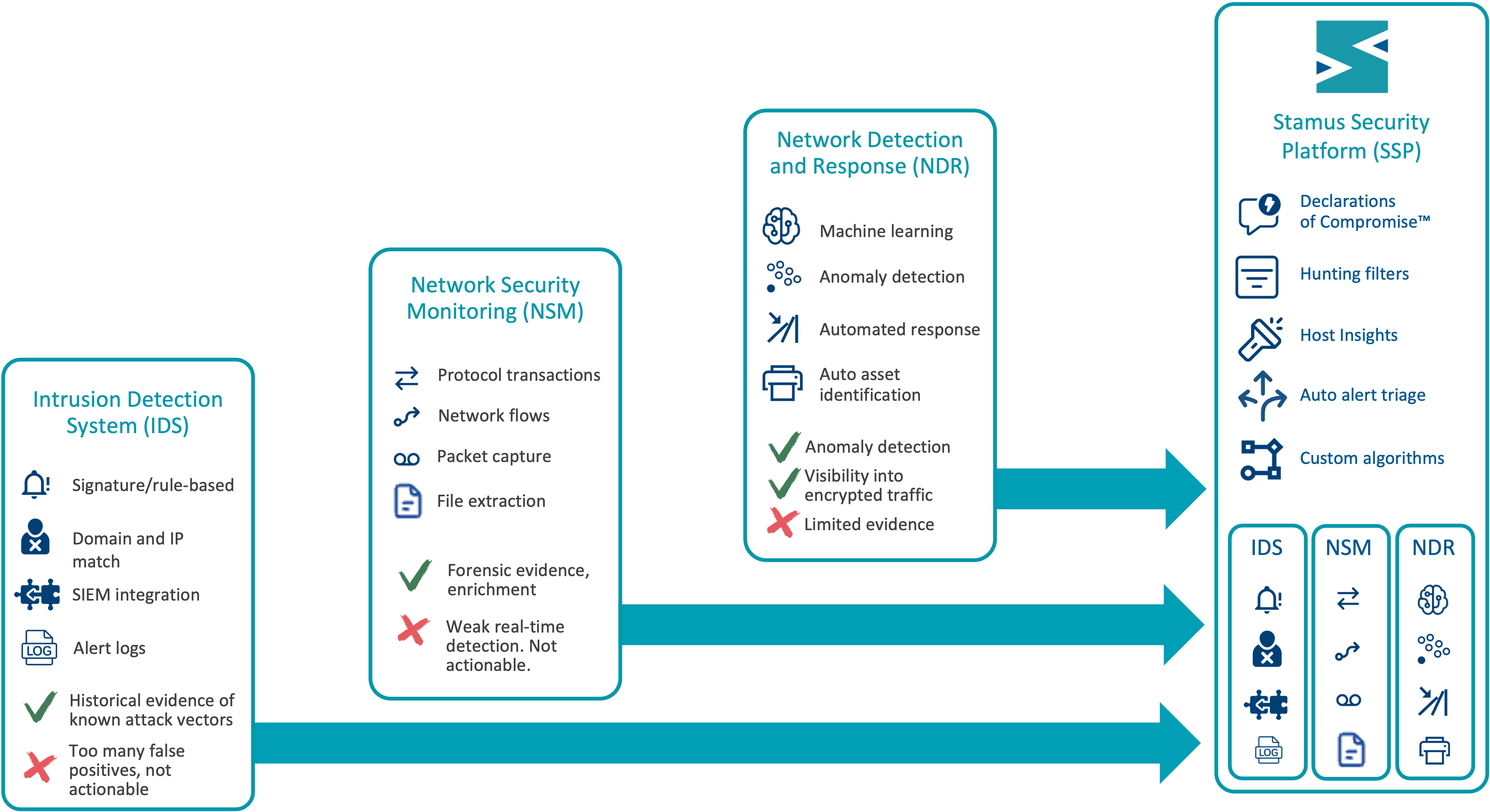
By combining the most powerful capabilities of intrusion detection systems (IDS), network security monitoring (NSM), and network detection and response (NDR), the Stamus Security Platform delivers a new generation of NDR that helps more-effectively uncover serious threats and unauthorized activity in a single consolidated solution.
Combining the Best of Capabilities¶
Intrusion Detection Systems¶
Intrusion Detection Systems (IDSs) passively monitor networks and compare traffic with a set of explicit signatures (rules) to detect attack signals in near real time. In addition, IDSs can identify suspicious or known-bad IP addresses and domains - indicators of compromise - that are regularly installed on the IDS as threat intelligence feeds. Both signatures and IoC matches generate alerts that can be logged as evidence or forwarded to a log management or SIEM for further analysis.
The benefits of IDSs include:
High-performance threat detection, suitable for monitoring network links up to 100Gbps
Extensive alert logs provide detailed evidence
Straightforward and customizable detection algorithms
Support for third-party detection rulesets and threat intelligence feeds
Can help organizations comply with industry or regulatory standards, such as PCI
The drawbacks associated with legacy IDSs include:
Widespread availability of IDS signatures sources require extensive tuning
Alert volume may overwhelm security teams with non-critical alerts, causing them to ignore or miss weak attack signals
They cannot natively detect many of today’s sophisticated threats
The alerts they log are missing contextual information needed to completely understand the event
Network Security Monitoring Systems¶
Network Security Monitoring (NSMs) systems also passively monitor networks and extract protocol transaction logs, file content, and other customized output for manual review in an analyst-friendly tool such as a security and information event management (SIEM) system. The output of NSMs can be correlated with the IDS alerts to enrich the evidentiary logs for incident response and threat hunting.
The benefits of NSMs include:
NSM logs provide a powerful set of flow-based information that can enrich the evidentiary logs for incident response and threat hunting
Generates the foundational metadata for advanced behavior-based threat detection algorithms
Provides mechanisms to analyze encrypted traffic using raw indicators like JA3,JA4+, and HASSH fingerprints, TLS ciphers
The drawbacks associated with legacy NSMs include:
They cannot natively detect many of today’s sophisticated threats
NSMs typically require extensive custom scripting to perform threat detection
The data generated by NSMs is not typically actionable on its own
Network Detection and Response Systems¶
Network Detection and Response (NDRs) systems also passively monitor networks and extract protocol transaction logs, file content, and other customized output for manual review in an
The benefits of NDRs include:
Modern NDRs are capable of identifying weak attack signals missed by other systems using machine learning and anomaly detection
Many NDR solution providers have pre-integrated their systems with tools capable of automating the response
Some NDRs can automatically identify network assets, categorizing them by type, brand, role, etc
The drawbacks associated with legacy NDRs include:
They often present vague alerts from mysterious detections with little evidence or explanation.
Most NDRs are closed systems that rely exclusively on the algorithms and threat intelligence of the vendor
Systems that are built primarily on machine learning algorithms often require months to baseline normal behavior
Stamus Security Platform¶
Stamus Security Platform (SSP) builds upon the best of all three technologies - providing the sophisticated detection and response capabilities of NDR along with the transparency, extensibility and evidentiary capabilities of IDS and NSM.
SSP provides additional capabilities that reduce time to detect and respond to incidents, including:
High-fidelity Declarations of Compromise™ (DoCs) are high-confidence and high-priority security events generated by Stamus Security Platform, signaling a “serious and imminent” threat on an asset. DoCs can be confidently used to trigger automated responses via EDR, SOAR, and other tools.
Guided threat hunting empowers users to investigate, classify, escalate, and automate vast amounts of event data, alerts, and contextual metadata using beyond the typical automated threat detection functionality of the system
Enriches security event logs with organizational context - such as internal network names, host names, and user names - to simplify and accelerate threat assessment and incident investigation
Host Insights™ tracks every host observed on the network in real time, giving analysts a rapid understanding of what HTTP User-Agents, TLS agents, user logins and so on, have been observed on each and every host.
Automated event triage - enabled by a tagging and classification workflow - to dramatically reduce the time spent by analysts reviewing security events
