Warning: You are viewing an older version of this documentation. Most recent is here: 42.0.0
Compromises¶
This section of Stamus Central Server offers a view on threats activity in your environment.
Impacted Assets¶
This page allows viewing which asset is under attack and by which threat. An asset can be impacted by one or more threats.
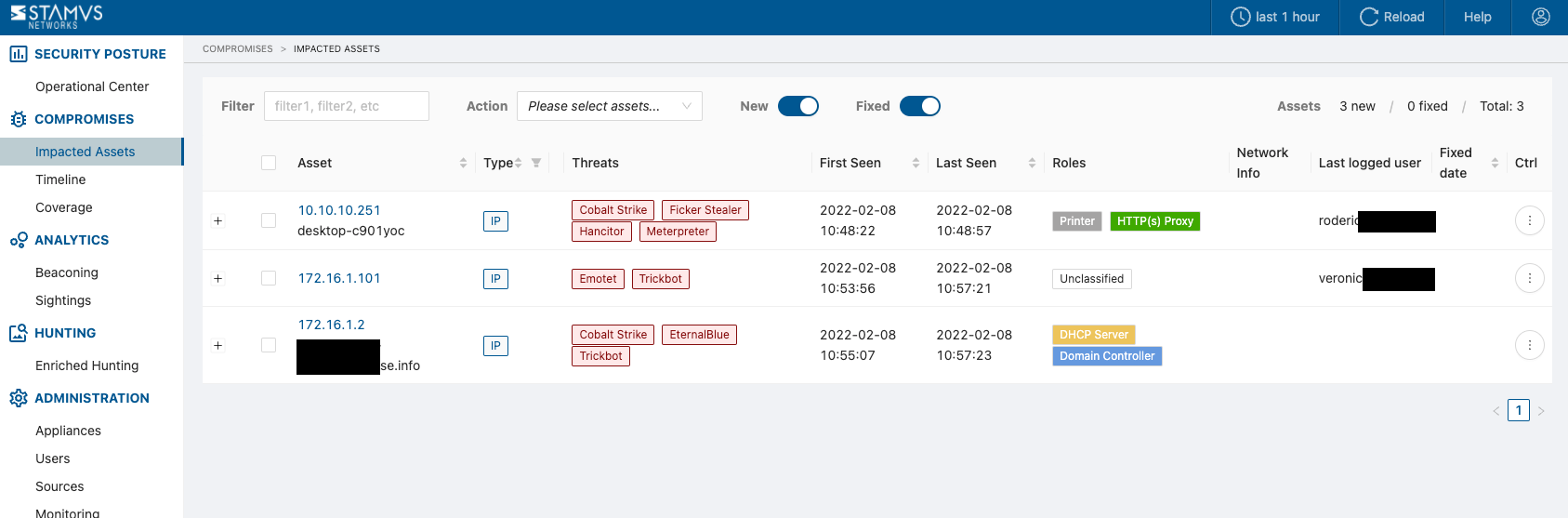
The table allows:
Filtering on different Assets (by using the Filter input field)
Performing Actions on Assets from the
Actiondropdown menu, likeAcknowledgeand/orRevertSwitching between
NewandFixedAssets list viewCounters for
new/fixed/totalAssets (Note that when using theNewandFixedswitches, Total count is aggregated, based upon the selected switch).Sorting in asc or desc order, and also - by
Asset Type(either Username, Email or IP)- Information on:
Asset HostID information- by clicking on the Asset linkThreatsfrom which the Asset is part ofFirst SeenandLast SeenNetwork info- if availableLast logged user- if availableFixed date- it is displayed only for a Fixed / Acknowledged Assets
Ctrl button - allows you to Acknowledge or Revet an Asset
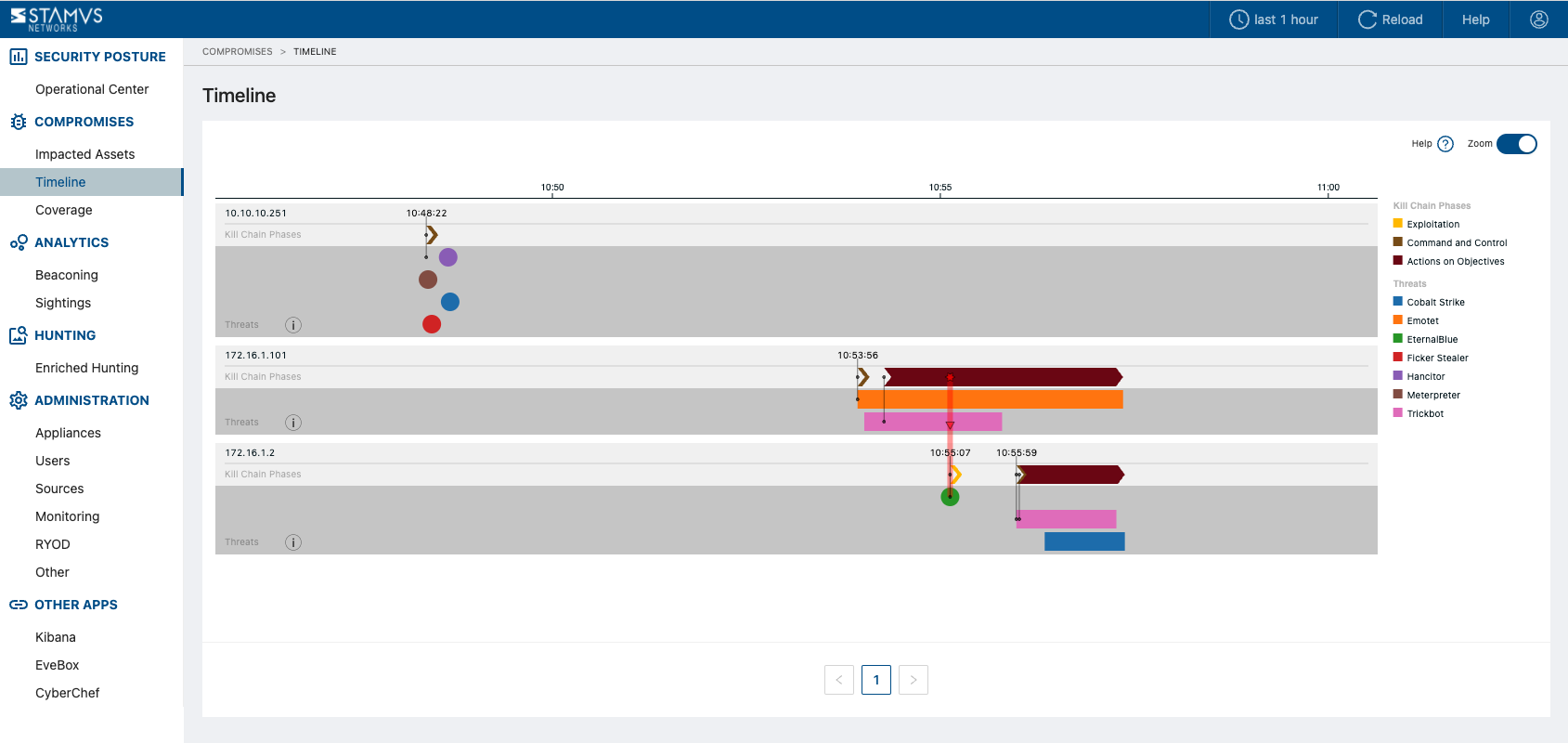
Timeline¶
The threat timeline lets you see what happened and when as well as observing lateral movement between hosts if it occurred (as illustrated by the following screenshot, see red arrow moving down from one host to another).
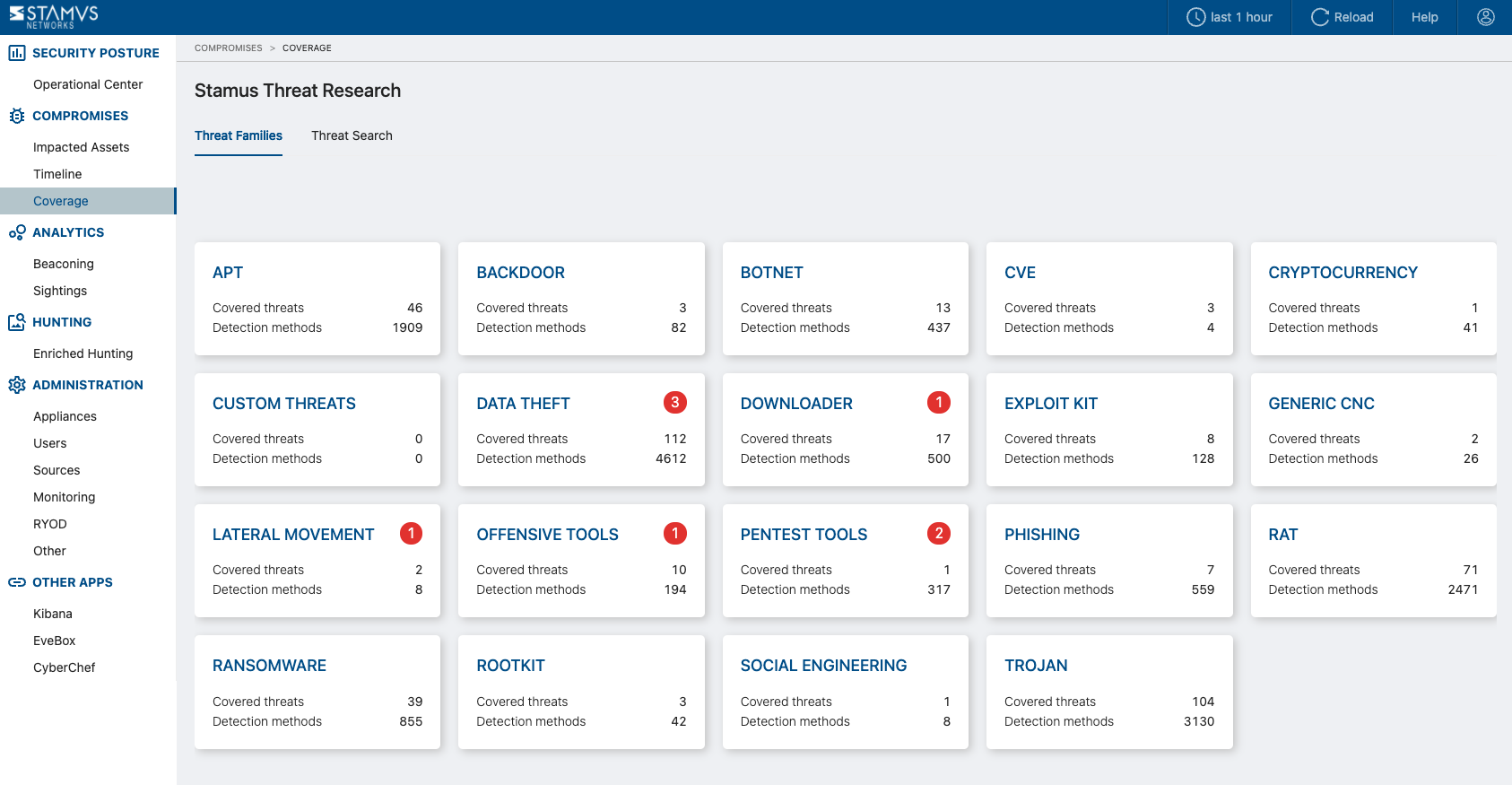
Coverage¶
The coverage page lets you see, and search, what threats are covered by Stamus Central Server. A detection method being a means of detecting a threat and each threat being detectable by one or more detection methods.